There are many things to consider when making a strategic purchase—like price, quality, and innovation. When it comes to data security, trust is a critical factor to consider. A security breach strikes at the heart of your credibility as a business. If attacked, will you be able to serve your customers? Or protect their information? What’s the impact on your revenue? Will you be able to recover? If you can’t trust the technology and partners you work with on security, then what?
With the constant barrage of cyberattacks, it’s not a question of if, but when you will be attacked. The best defense is to have a cyber resilience plan. There are three distinctly different approaches you can take to building and implementing that plan:
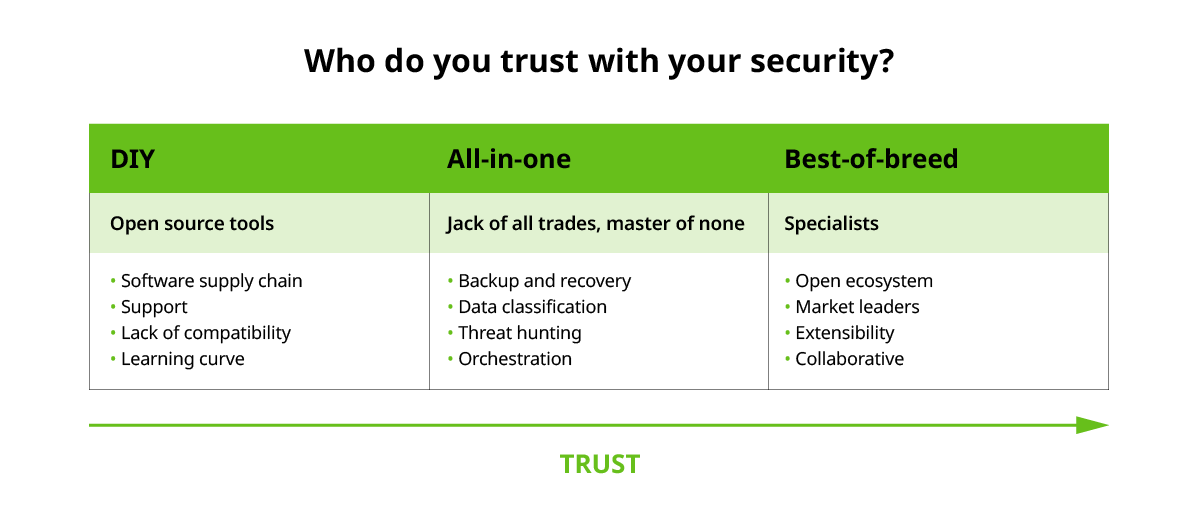
- DIY: Literally do it yourself. Trust no one else. Keep it all within your control. Price may be your primary driver here.
- All-in-one: Pick an off-the-shelf solution built for breadth, not depth, making it adequate for most things but not great at any one thing. We call this the jack-of-all-trades approach. Value may be your primary driver here.
- Best-of-breed: Handpick the best solution for each problem space, be thoughtful about your specific requirements, and trust that the best solutions will be the best for a reason. Trust and reputation may be your primary driver here.
Let’s consider the three approaches above in the context of building a house. In DIY, you could decide to be your own contractor, architect, and builder and build your dream house. In an all-in-one, you can keep it easy. Buy an RV and be done with it. In a best-of-breed, you hire a separate architect, contractor, and builder based on their reputation and the quality of the work you’ve seen from their other builds. Note, there’s no right or wrong answer in this scenario—this is your home, so do what meets your needs.
Building a cyber resilience plan you trust
Navigating the different approaches when building your cyber resilience plan can be daunting. Each approach will have its own tradeoffs. Let’s examine those tradeoffs.
DIY
Building your cyber resilience solution will likely combine commercial and open-source solutions. While open-source software has become the foundation of many of today’s applications, they bring risks and challenges to security, specifically around the supply chain. Questions like, how do you know where the code is coming from? Or, where will you get the support for those tools, and what will happen if the people who built them aren’t available?
Understanding what’s in your open-source code and how to manage the potential risks will help you address security weaknesses and vulnerabilities. But it’s safe to say, it would take lots of time to vet those open-source tools and lots of resources to maintain them. Can you really afford trial and error in an enterprise security context?
All-in-one
Using a security solution that claims to do it all may be attractive from the perspective of simplicity. But if the integrated functions themselves aren’t fit-for-purpose, this could mean a serious tradeoff. Security is a complex area. Across endpoint, perimeter, applications and data, there’s a lot to consider and the depth of capability you need in each of those areas is critical.
With less fuss, a jack-of-all-trades, master-of-none approach might get a “security” roof over your head faster. Still, the reality is that not all the capabilities will be top-of-the-line. Why? Because that vendor is spending their precious engineering resources across too many problems.
Best-of-breed
Finally, you could use the best market leaders in their respective areas. Utilizing an open ecosystem that allows these best-in-class solutions to integrate and your teams to collaborate—gives you depth and breadth. This customized strategic approach leverages unique security capabilities to meet your organization’s security needs.
Back to trust
This is where the need to believe and trust that a brand can deliver on its promises comes back into focus. In the first scenario, a DIY approach means you rely heavily on your team’s abilities and skills with the question of trust that lives upstream in the vetting of open-source software.
With the best-of-breed approach, you’re getting the best vendors in each of their respective areas and ensuring, through the right combination, they’ll work together to achieve your business goals and security outcomes. Essentially, you’re trusting a federation of collaborating brands to provide the most tailored solution.
The all-in-one generalist, on the other hand, is the trust outlier in this scenario. You’re betting the generalist is devoting the same amount of resources to each specialist leader’s separate areas in their respective functions. Are you trusting that each specific function and outcome will be good enough? Can you really trust good enough when it comes to your organization’s security?
An informed security decision-making process
Please don’t take our word for it. Below are five additional considerations when making an informed decision for a data security vendor.
- Process: Your security organization has well-defined processes for monitoring, detection, response, etc. How well does a vendor fit with these? Is it complementary to them? How does it enhance and extend them?
- Alignment: The threat landscape is constantly evolving. As are your needs (clouds, workloads, etc). How is this potential investment future-proof? How extensible is the platform?
- Product: Will this solution allow for integrating tool chains between infrastructure and security? Will it facilitate automation, reduce or remove human error, and increase the fidelity of data insights?
- Services: Building a resilience plan is a business need. It sits above any single silo of technology. Are there consultative partners that can help you integrate and build this to meet your business needs?
- Incident collaboration: When an incident occurs, the proper response takes coordination and collaboration amongst a team of different partners. Can you count on a team approach from this vendor should an incident occur? Are they likely to go their own path?
Understanding the benefits and trade-offs of each approach will help you make a more informed decision about your cyber resilience plan and which vendors to consider as part of that plan.
Next steps in your cyber resilience journey
Looking to other independent voices, organizations, and channels can also help you validate your choices for vendors to be considered. One great example is the Data Security Alliance. It combines best-in-class solutions from industry-leading cybersecurity and services companies, including BigID, Cisco, CrowdStrike, CyberArk, Okta, Palo Alto Networks, Securonix, Splunk, Tenable, Netskope, ServiceNow, and Zscaler with security advisory relationships with Mandiant and PwC. Of course, Cohesity is proud to add our name to this distinguished list of leaders committed to solving security complexities that one vendor can’t solve alone.
Finally, if you’d like to jump-start your planning for a cyber resilience plan, there may be no better way than joining an upcoming Ransomware Workshop. Join Cohesity and our Data Security Alliance partners in a fully immersive 2-hour workshop that places you in the middle of a live ransomware attack. You’ll adopt the persona of a C-level decision-maker in a fictional company, with the challenge to limit the business impact as events unfold and to build your own resilience roadmap as part of the session. See when a live workshop will be in your area.