In my many years leading response to data theft and destructive cyberattacks, I learned the value of having a “jump bag.” The term, as old as my career in incident response, originally referred to a physical container that held all of the hardware and software we needed to pick up on our way to a physical location that suffered an attack to gather evidence and investigate the incident. The idea is to be prepared to respond immediately—rushing around to find everything you need while under the pressure of an incident wastes valuable time and leads to forgetting something essential.
Jump bags, then and now
Fast-forward to 2024, and the “jump bag” is more important than ever for those trying to investigate, mitigate, and recover from cyber incidents. For most of my career, the threat we faced was almost uniquely data theft, which wasn’t really “theft” at all. It was the unauthorized disclosure of data—we still had a copy of the data, which allowed us to continue to deliver the mission of our organization. Our impacts were largely reputational damage, potential litigation from impacted data subjects, and supply chain and regulatory fines.
However, with the advent of destructive cyberattacks, such as ransomware and wiper attacks, where the organization can no longer deliver its products and services, losses now scale linearly. Every second spent on response and recovery can impact a victim organization’s viability. It is not just that jump bags are more important than ever before. The nature of its contents has also changed, reflecting the changes in the way we deliver IT over the past four decades.
I remember dealing with some of the earliest malware in the 1980s, and the jump bag was typically a rucksack or a pelican case. Sometimes, even five pelican cases in large government networks. These contained the resources needed to run response activities with my team.
Jump bag checklist—back then
Here’s a list of what was in our jump bags back then:
Today, we live in a world of remote acquisition, end-point and extended detection and response (EDR/XDR), virtual machines, and cloud instances. Jump bags can still be physical containers we take on-site, but today, these physical ones will likely be augmented by a “virtual jump bag,” the tools required for remote acquisition and analysis.
So, what would a best-practice jump bag look like in 2024? The exact nature of what goes into your jump bag is highly contextual based on your incident response workflow and the way your organisation delivers its IT services.
Jump bag checklist—today
There are, however, several standard tools that I have observed being used by organisations that have resulted in better response and recovery outcomes:
Relying on the downloading of tooling post-incident is not a good strategy. Adversaries may have compromised your network infrastructure and could hamper attempts to do so. The trend has been for incident responders to increasingly rely on remote agents for detection and response activities, such as searching for indicators of compromise and forensic acquisition. Some of the challenges to this approach are that after an incident, any incumbent tooling on the end-point can never be 100% trusted. Popular incident response frameworks, such as NIST SP800-61 and the SANS Institute Six Step Incident Response Cycle, recommend the containment of the spread of an incident by isolating hosts and networks that would limit their functionality in response.
The tooling required to respond and recover from a destructive cyberattack isn’t just traditional security tooling, as core IT infrastructure is also likely impacted. Services like email, DNS, certificate authorities, identity and access control, voice-over-IP, and even physical access systems may be impacted and need to be brought back to a trusted state before you can coordinate and communicate response efforts with external third parties and internal stakeholders. This is commonly overlooked in crisis response plans for ransomware.
The first is acquisition footprint: How much impact does acquiring the evidence have on the system being investigated? In other words, if we need to install software to acquire evidence, does this software change the evidence?
The second area of concern is maintaining a chain of custody to ensure that evidence isn’t changed from the original during its lifecycle. In physical disk acquisition, we solve this problem by using write blockers to prevent changes to the file system of the original disk and placing the original disk in a Faraday bag, locked in an evidence safe. At the same time, we only work on a working copy.
Remote acquisition is almost always a trade-off where we almost always need to deploy some software on the end-point, which results in the end-point file system being changed in order to obtain a copy of the remote disk’s contents. Some organizations do pre-deploy acquisition capabilities onto their end-points in advance of an attack, but this in itself represents an extended attack surface that attackers can use against systems or can be evaded by the adversary during the attack.
Another challenge with remote acquisition is that the first stage in most incident workflows for destructive cyberattacks like ransomware and wipers is isolating compromised systems. This results in an inability to connect to the systems, requiring a physical presence to either place the system into an isolated network or to remove the disk for acquisition.
This is where backup snapshots provide a lot of forensic value. They already exist in a central location and, in addition, provide not just a snapshot of a system after the attack but can show the changing state of a filesystem over the duration of the attack.
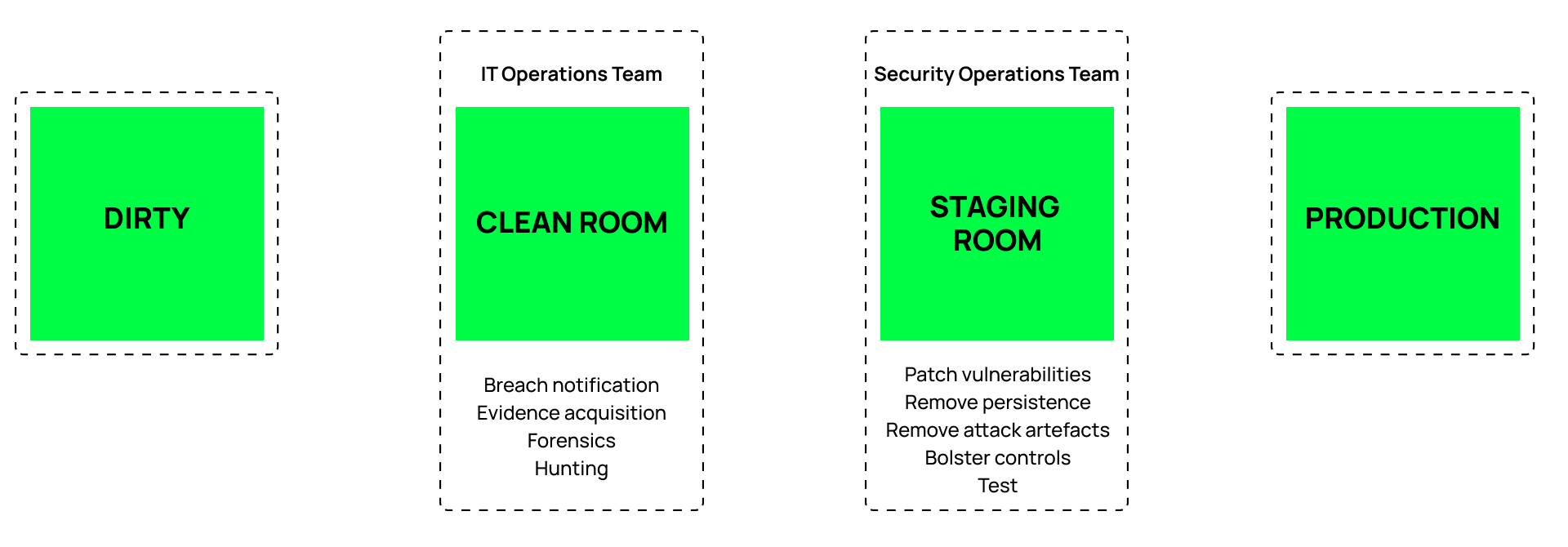
In the case of Cohesity, we recommend the customer has four networks:
Any physical jump bag should include the network equipment required to establish these isolated environments. With a virtual jump bag, the golden masters of the network configurations to create these isolated environments should be held on immutable storage, cryptographically hashed, and ready to be deployed in minutes.
Cohesity has a design blueprint and associated workflows that organizations can leverage to prepare for establishing these clean and staging room environments in advance.
How Cohesity helps build your jump bag
Establishing a Minimum Viable Response Capability with the trusted tooling you normally have in your jump bag is a core feature of Cohesity’s Clean Room solution. It combines native response and recovery capabilities designed to continue to function after a destructive cyberattack with a collaborative approach with an organization’s existing security operations toolset.
The Cohesity Clean Room solution provides design blueprints and associated workflows that organisations can use to:
Cohesity allows organisations to establish a vaulted immutable store for incident response workflows, contact lists, trusted software images, licence keys, and other digital assets required to respond to the incident. Cohesity FortKnox ensures that this can sit off the organisation’s core IT infrastructure beyond the reach of adversaries. The Cohesity SmartFiles functionality allows resources to be rapidly mounted and used by the native orchestration and scripting tools to start a response within minutes.
The acquisition of filesystem evidence at a file and directory level is simplified using Cohesity DataProtect. Incident responders can examine file systems over the incident timeline and extract configurations and binaries for further analysis. DataProtect’s file system’s immutability and integrity provide a strong chain of custody to help prove the validity of evidence. As DataProtect isn’t reliant on access to the victim system over the network, these forensics capabilities continue to function even if containment measures to isolate networks and hosts are in place. There is no additional agent to install, as the response and recovery functionality is provided by simply backing up your data into a Cohesity solution, thereby reducing the attack surface and the opportunity for evasion.
FortKnox and SmartFiles can further be used to store captured forensics artifacts, ensuring they’re held beyond the reach of adversaries and in a store with a strong chain of custody.
Cohesity DataHawk’s threat-hunting capability allows organizations to leverage a curated cyber threat intelligence feed of hundreds of thousands of Indicators of Compromise used by destructive cyberattackers to hunt for evidence on file systems without the need for an active network connection, decreasing the adversary’s ability to evade detection and allowing hunting even if networks and hosts have been isolated to contain a destructive cyberattack. Customers can augment the included feed with their own threat intelligence providers or threat intelligence platforms.
If you’re interested in learning how Cohesity can help you develop and deploy a clean room environment and jump bag, sign up now for our ransomware resilience workshop.