Are you properly securing connections even when accessing or managing internal network resources/workloads such as Cohesity clusters? Is securing internal connections to resources even necessary? My experience administering and managing internal resources/workloads, especially over the last few years, has taught me no matter the location, cyberattacks can and will happen. Whether resources or workloads are in the cloud or a private data center, using SSL to help protect and secure connections is vital, especially to our backup environments which help us recover in the event of an attack such as ransomware. Today, let’s look at a few tips about securing connections using SSL certificates as well as updating SSL certificates on a Cohesity cluster.
Tips for securing connections using SSL
Securing connections using SSL certificates might not be the most straightforward process at times, but it is a tried and true way to secure connections to network resources/workloads. These days, figuring out what certificate formats, authentication types, such as Extended Validation (EV) Organization Validation (OV) Domain Validation (DV), encryption strengths 128 vs. 192 vs. 256 bits, can vary widely depending on the resources/workloads which need to be secured. Rule of thumb is to use 256 bit SSL encryption but always refer to vendor documentation for system requirements, especially with legacy systems which may require a less secure level of encryption or different formats such as PEM, PFX, etc. Lastly, refrain from using wildcard certificates for some or all of your resources/workloads, instead use individual certificates created for each unique workload.
How to update SSL certificates on Cohesity clusters
In order to get started with your SSL certificate on a Cohesity cluster, you will need to have the following tools on your Windows or Mac computer: WinSCP, Putty, a Cohesity support user account, as well as IRIS_CLI admin access to any Cohesity node within the cluster.
In the example below, we are renewing an internal certificate created previously using our Active Directory Certificate Services server for our cluster. OpenSSL program is being used to create the two PEM formatted certificate files needed.
- Open the program WinSCP used to upload the certificate files.
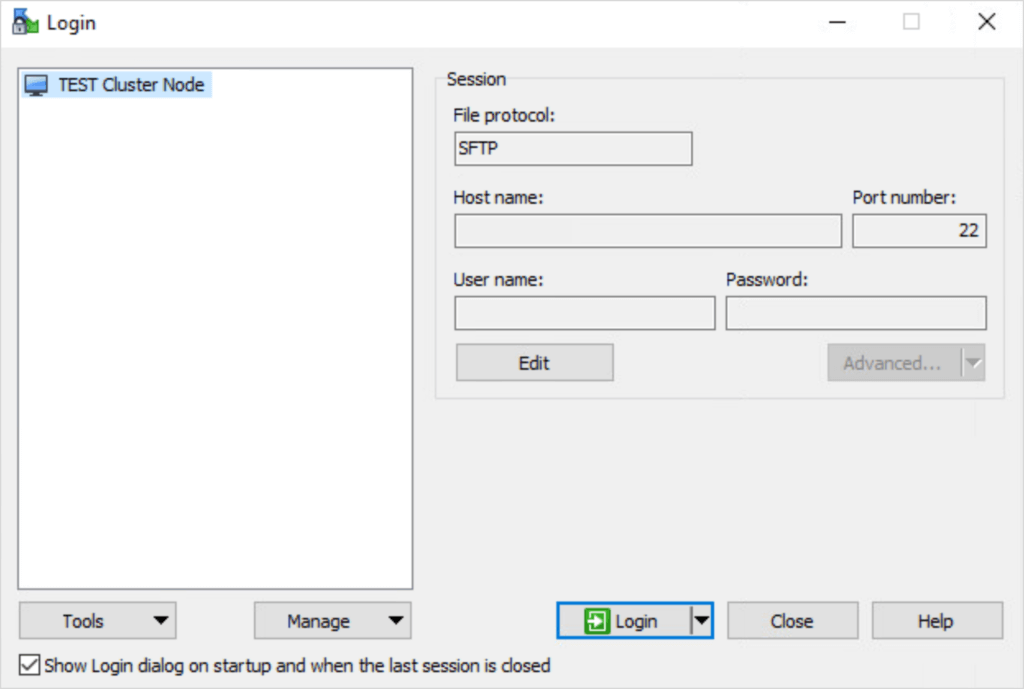
Note: The Cohesity support user and password will be needed for this step.- Open a session to the Cohesity cluster node using the Cohesity support user and password.
- Enter username and password.
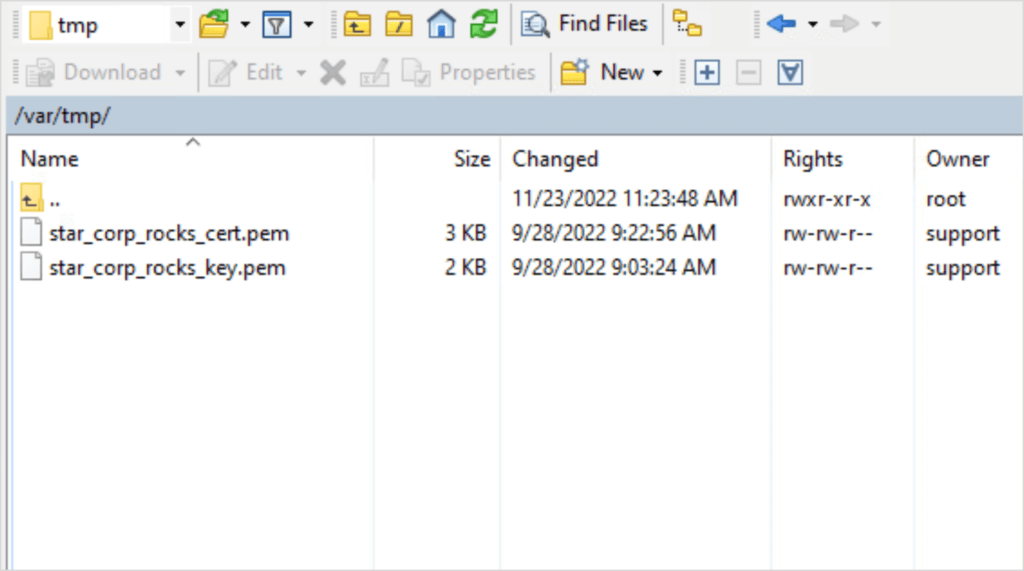
- Copy the certificate and key PEM files over to /var/tmp on the Cohesity node. Verify that the files have successfully copied over to the node.
- Open a session to the Cohesity cluster node using the Cohesity support user and password.
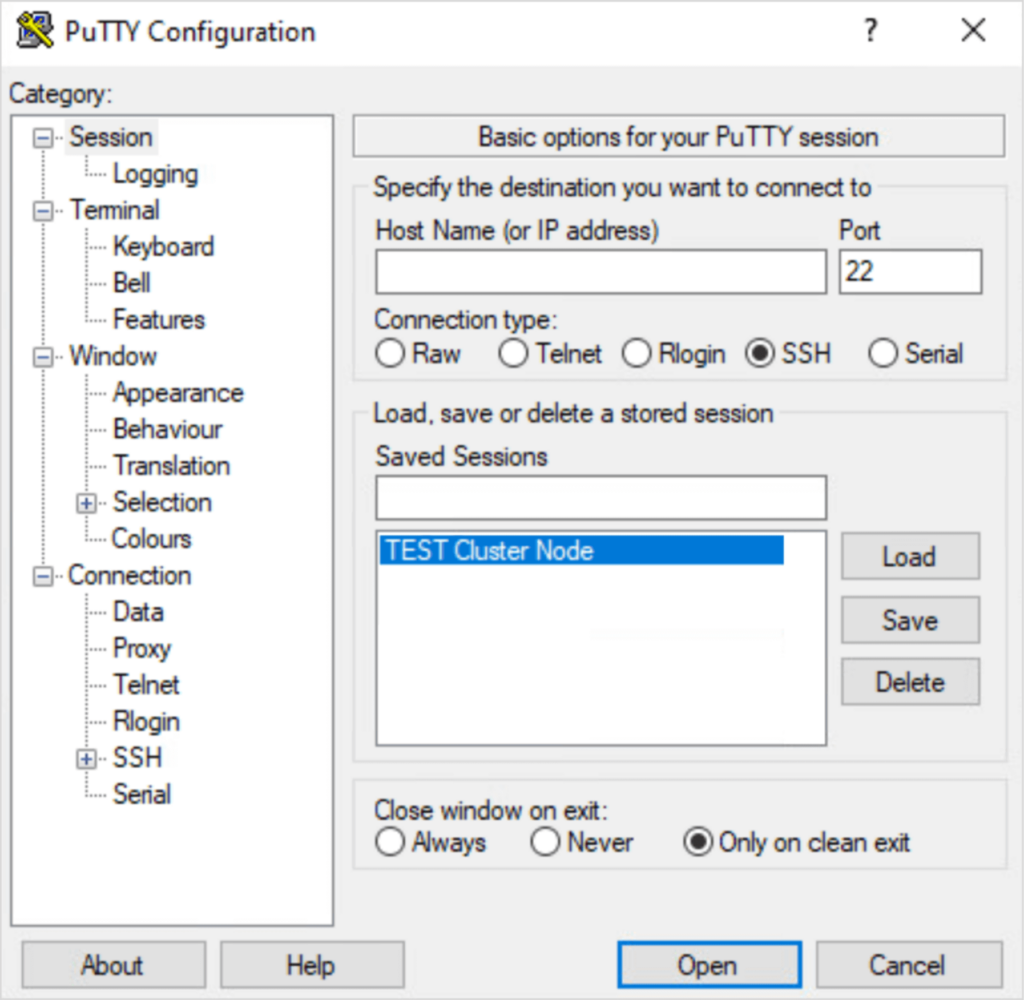
- Now that the certificate files are copied over to the node, let’s SSH to the node using a Putty terminal.
- Open Putty and terminal into one of the Cohesity cluster nodes.
- Enter the username and password.
- Open Putty and terminal into one of the Cohesity cluster nodes.
- Now we need to run iris_cli and log in as local admin.
- Now run this command to import the new certificate and key files.
- cluster update-ssl-certificate ssl-certificate=/var/tmp/SSLcert.pem ssl-cert-private-key=/var/tmp/certkeyfile.pem
- Lastly, execute the commands below to apply the updated certificate for the Cohesity cluster.
- cluster restart-services service-names=iris
- cluster restart-services service-names=bridge
Wrapping up!
Securing your internal connections to resources/workloads is very important in our current cybersecurity climate. Using SSL certificates is an easy way to secure internal connections to resources and workloads, and can be very cost-effective as well. We’ve seen how easy it is to secure connections to Cohesity cluster resources using certificates created and managed using Active Directory Certificate Services. Certificates might seem daunting at first, but they do not have to be. These little nuggets of knowledge should help you update your SSL certificates on Cohesity clusters with ease.