We recently announced new updates and functionality for our cyber recovery assistant, an AI-powered assistant for investigating and triaging items that have triggered alerts in the Cohesity Security Center.
Cohesity Data Cloud already uses several built-in AI capabilities to rapidly detect, investigate, and respond to potential threats within the environment, enabling faster recovery of operations.
Our new clean room design and recent enhancements to threat detection and data security posture enable customers to confidently and efficiently move from alert to recovery with a guided incident response wizard.
The enhanced AI-powered cyber recovery assistant tool for the Cohesity Data Cloud provides expert guidance on the appropriate response. Generative AI uses security context as input and complements this with multiple sources, including threat-hunting scans, ransomware detection, data risk, and posture. Customers can receive an alert for anomalous behaviors.
We will run through a typical scenario below to illustrate the cyber recovery assistant’s capabilities and value.
What does the Cohesity cyber recovery assistant do?
The user begins with the Cohesity Security Center, which provides an integrated dashboard to monitor security alerts, threats, sensitive data exposure, data isolation status, and the security posture of our platform, Cohesity Data Cloud. In this dashboard, customers will see their Posture Advisor Score, when the latest scans were completed, and the top issues found.
Anomaly detection
In this scenario, our backup admin notices an alert for an anomaly in the dashboard. Cohesity’s anomaly detection capabilities use machine learning algorithms and AI to analyze data change patterns and detect unusual activity. However, just because there is an alert does not mean that the anomaly is a sign of a ransomware attack—it does mean further investigation is needed.
As we manually review the alerts and trend analysis reports, we see that a large number of files have been changed or deleted, which indicates that there could be ransomware—which needs further analysis. To dig deeper into this, the backup admin needs more help understanding the anomaly and starts the cyber recovery assistant.
Recently updated, the AI-powered cyber recovery assistant allows the admin to converse with the Cohesity system to assess the impact of the anomaly-correlated event, get direction on the next steps of investigation, and perform any remediation that may be needed–all from within the wizard without needing specialized cyber response expertise.
At this point, the user understands the nature of the anomaly but has yet to learn of its impact or what the next step should be.
From the chat interface, the admin can start asking natural language questions:
- What does an anomaly mean?
- What was the anomaly observed here, and on what object?
- What is the confidence level of the anomaly?
- What were the files changed?
- Has this type of anomaly been seen before? And when?
By being able to ask these questions (and more), the admin can begin collecting information and clues about this anomaly, which will help determine what to do next.
Understanding impact:
Chatting with a cyber recovery assistant is similar to having a conversation with a person—the admin can ask more detailed questions and drill deeper into the analysis of the alert.
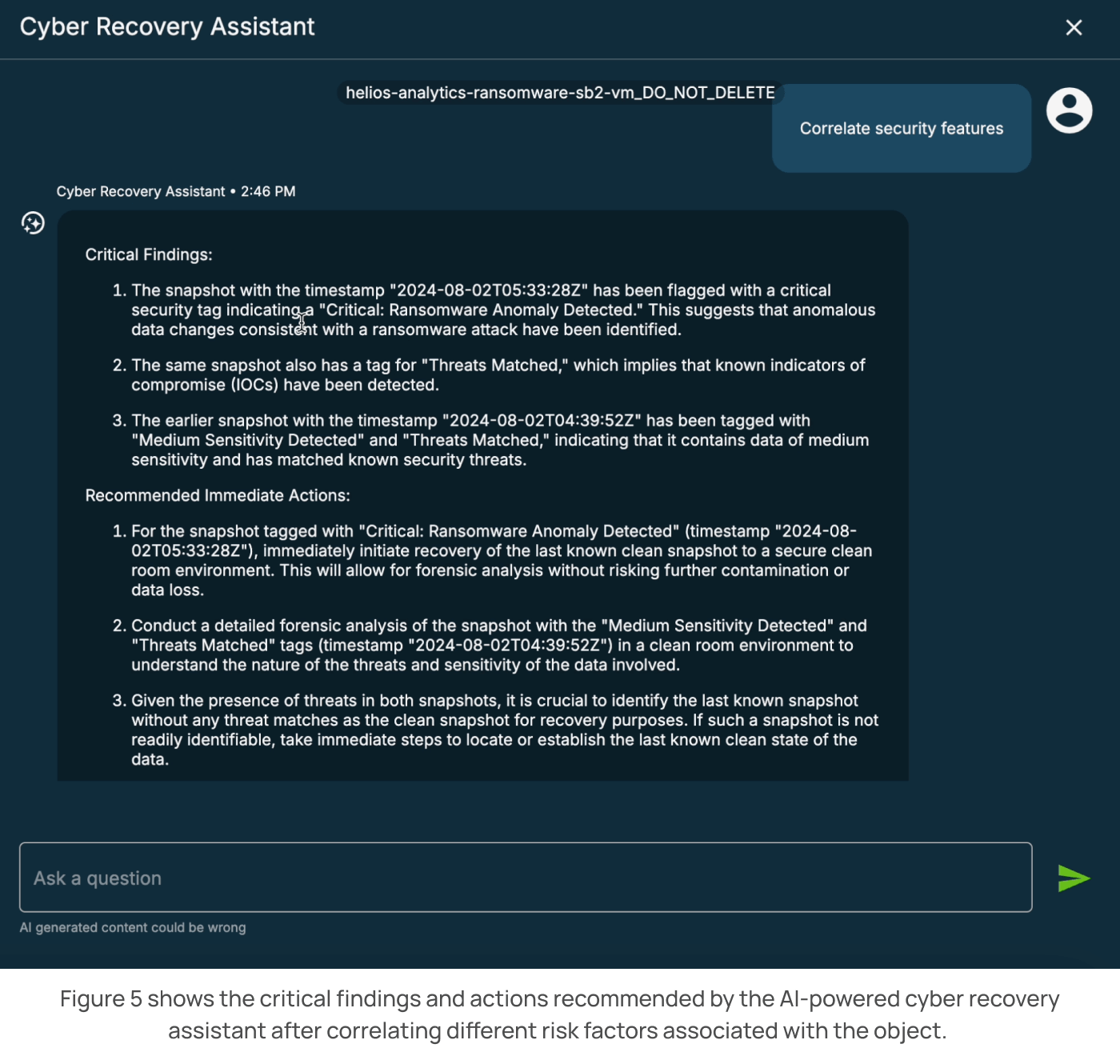
In this scenario, we need to understand the impact of this anomaly to fully assess the risk and determine how to proceed. The admin can use the assistant to analyze and correlate the security context and present an impact assessment analysis. We’ve asked the assistant to check whether the object impacted had sensitive data containing personally identifiable information (PII) and whether it was properly backed up or vaulted to Cohesity FortKnox.
The assistant can analyze whether any previous threat scans were performed on this object and whether a history of threats was detected. In this scenario, the assistant notifies the admin that the anomalous object has sensitive data and is also being vaulted into FortKnox. Since sensitive data is involved, the admin knows this issue should be escalated to their SecOps team. SecOps can quickly implement measures to isolate the threat and ensure that the server has the appropriate security policies for hosting sensitive data.
Recommending and performing additional scans to investigate the issue
The cyber recovery assistant can recommend actions that can be initiated from the chat interface.
In this scenario, after the admin has investigated, the assistant recommends running a Threat Scan or a Data Classification scan if one was not previously performed. The admin can start the process based on the information previously collected by the assistant.
With this confirmation about the presence of malware, the admin now has the confidence to escalate this issue to SecOps by creating a ServiceNow ticket. Upcoming versions of the cyber recovery assistant can run these investigative scans and report back with results (for example: “malware found in object indicating a possible ransomware attack”) within the same chat interface.
Alternatively, the admin could initiate a playbook on the customer’s chosen SOAR platform. A SOAR playbook provides security operations teams with a checklist of actions to take when dealing with a specific security issue. This allows the team to respond quickly and effectively, often utilizing tools to resolve the issue more efficiently and reduce human error.
For instance, in the event of ransomware, they could use a SOAR playbook to identify ransomware activity or employ DLP tools to detect data exfiltration. In the case of Cohesity, SOAR playbooks could be utilized for backup and recovery or to create a ticket in a system like ServiceNow.
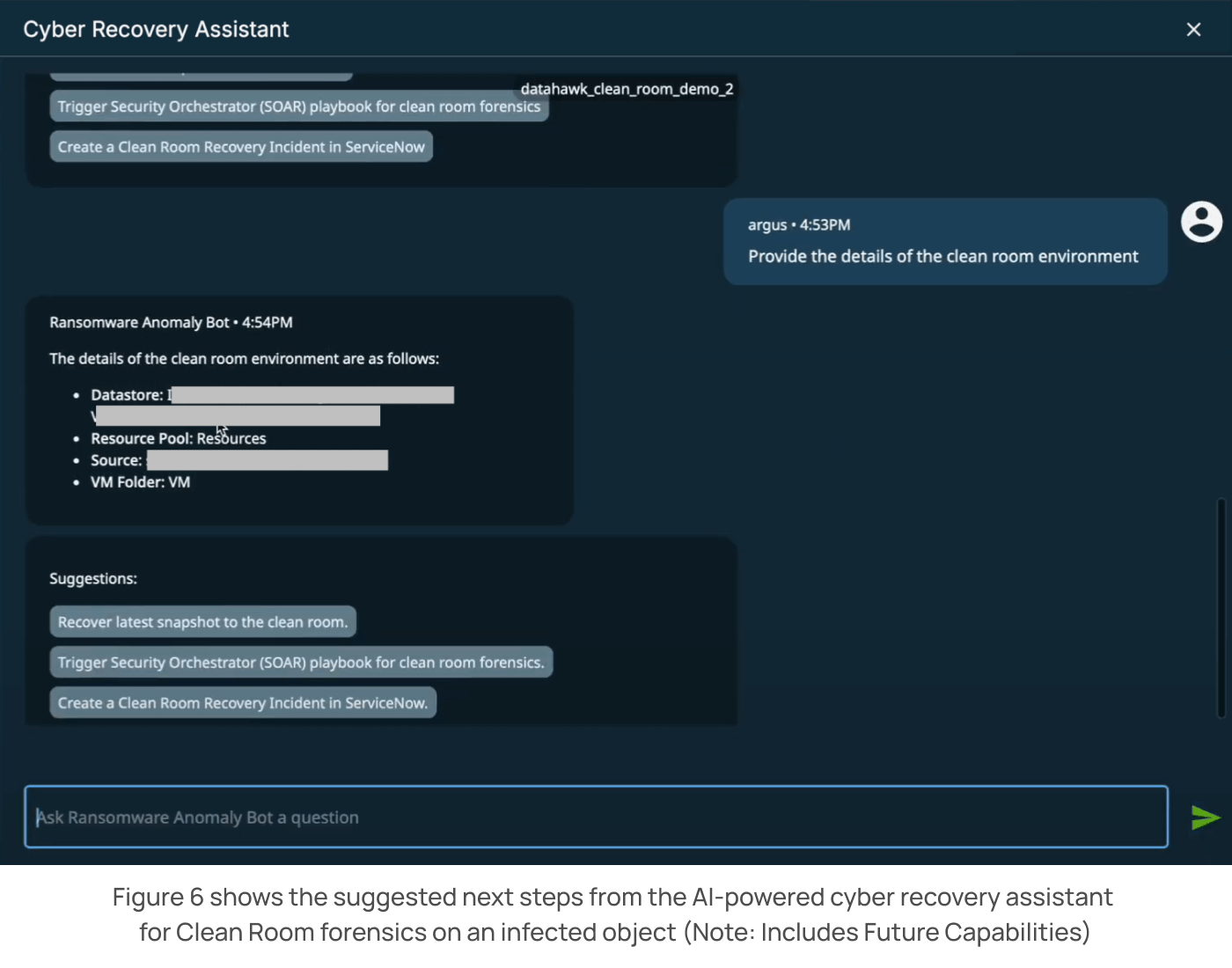
Move the workload to a clean room
In the coming months, we expect to introduce these additional functions to our cyber recovery assistant:
- The ability to orchestrate the movement of a workload to a designated clean room.
- The ability to initiate the creation of a ServiceNow ticket for examining an infected object.
- The ability to trigger SOAR workflows for investigating the infected object.
Cohesity’s clean room design provides a trusted and proven foundation that speeds incident recovery and augments investigations by Security Operations teams while minimizing the risk of secondary attacks. The modular design helps isolate the attack or breach within minutes and provides several native capabilities to support the SecOps team’s needs in the clean room investigation.
Cohesity DataHawk’s threat-hunting capability provides incident responders with a curated feed, helping the organization understand the adversary’s techniques throughout the attack’s lifecycle, interacting with engineers in real time and real language.
Cohesity DataProtect delivers rapid access to system snapshots over the incident timeline, allowing forensic analysis of filesystems and evidence collection. With a better understanding of the incident’s full scope, teams can mitigate threats faster, allowing customers to return to regular business as quickly as possible.
Learn more about our cyber recovery assistant
The initial release of the cyber recovery assistant is available for no additional charge to current data protect customers. Additional functionality is available when combined with Cohesity DataHawk. Contact your sales rep to activate the cyber recovery assistant or get more information about Cohesity DataHawk.
The additional clean room orchestration and other AI-powered features and functionality will debut in upcoming releases.