Ransomware attacks and data theft can feel like a torrential downpour to businesses. As we mentioned in our blog “Protect Your Data in the Ransomware Storm,” cybercriminals have continued to evolve over the years, and are now targeting backups and exfiltrating mission-critical data to hold hostage. Organizations worldwide are not only having trouble keeping up with their tactics, but also effectively protecting their most valuable data.
In June 2021, St. Joseph/Candler (SJ/C) hospital system experienced a ransomware attack that impacted 1.4 million individuals. SJ/C, one of the largest healthcare providers in Georgia, determined that hackers first gained access to their systems on December 18, 2020, deploying the ransomware attack on June 17, 2021. Further investigation revealed that files containing patient information such as addresses, dates of birth, social security numbers, driver’s license numbers, patient account numbers, financial information and more were compromised. The ransomware attack not only led to potential HIPAA violation fines, but SJ/C suffered several patient lawsuits and ultimately significant impact to their reputation and brand.
The Ireland public healthcare system, Health Service Executive (HSE), faced a similar attack in May 2021. Investigation showed that hackers gained access to the network two months before the ransomware attack.
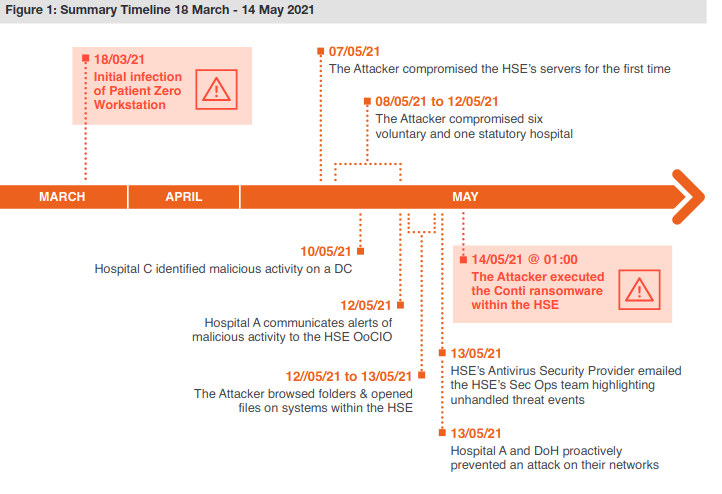
The first sign of trouble was on March 31, 2021 when antivirus software detected malicious software running on a workstation. But, because the antivirus software was only set to monitor, it did not remediate the situation and actively defend against the rogue software’s actions to spread further. On May 14, 2021, the hackers deployed Conti ransomware throughout HSE, disrupting services to hospitals and leading to a near complete shutdown of HSE. The impact was devastating – HSE was forced to cancel up to 80% of healthcare services and clinic appointments in the days following the attack and reported that recovery costs for the ransomware attack would exceed $600 million.
So how does a business protect what matters most?
Build a Solid Recovery Foundation
The first step towards protecting your sensitive data is by ensuring that you have a comprehensive backup and recovery solution in place that can restore your production workloads in minutes. As we learned in our blog “Protect Your Data in the Ransomware Storm,” one of the first types of attacks cybercriminals have made is targeting production data and encrypting it to hold it hostage. If an organization has a clean backup copy of data when a ransomware attack hits, they can easily recover production data that is being encrypted.
We believe the right backup and recovery solution integrates simplicity at scale, zero trust security principles, AI-powered insights and third-party extensibility to enable organizations to protect their data from ransomware attacks. With the ability to ensure immutability and proper access controls at the platform level, cybercriminals would be unable to reach the data in the first place.
Add An Additional Layer of Protection
When it comes to further safeguarding sensitive and proprietary data, organizations are turning to data vaults. These solutions enable businesses to store data in isolated (think virtual “air-gap”), immutable environments that are separated from their primary and secondary storage infrastructure, providing an extra layer of defense against ransomware attacks with a tertiary copy of recoverable data.
Cohesity has introduced Project Fort Knox, a SaaS offering that delivers Cohesity-managed data vault capabilities by allowing customers to achieve data isolation through a cloud-based repository. The vaulted copy of data on the AWS Cloud can be used to rapidly recover data that has been lost or compromised back to the source or an alternate location. In the event of a ransomware attack, an untainted copy of data can be easily identified, making the recovery process much faster. And, IT teams can prepare for cyberattacks by regularly testing attack preparedness with mock drills in this isolated environment in a manner that is otherwise difficult to do. With a comprehensive approach to data security available through SaaS, Project Fort Knox makes next-gen data isolation as simple as: connect, vault, and recover when needed.
Give Governance and Compliance a Machine Learning Assist
As privacy regulations continue to evolve, data governance has become a critical part of data management for organizations in heavily regulated industries such as financial services and healthcare. And compliance with privacy and protection laws has become even more challenging, with more regulations emerging every day.
Cohesity DataGovern1 is a data security and governance service that leverages machine learning (ML) to automate the discovery of sensitive data while analyzing access and usage patterns for potential cyberattacks. Available as SaaS, DataGovern enables organizations to:
- Prophylactically identify overexposed sensitive data with real-time scanning of source-side and backup environments. Encouraging proper access control hygiene deters attacks from happening in the first place.
- Automate and simplify data classification with predefined and custom policies and reporting for GDPR, CCPA, HIPAA and more.
- Detect behavioral anomalies in near real-time to determine unauthorized data sharing, and other risky behaviors.
With DataGovern, businesses would be able to simplify and automate data classification, easily detect suspicious behaviors and minimize their exposure to data exfiltration attacks.
Keeping Up with Change
The ransomware storm is only growing as more cyberattacks are launched each and every day. Now is the time to partner with Cohesity and take advantage of a unified portfolio for backup and recovery, disaster recovery, data governance and compliance, and data isolation solutions, all managed by Cohesity and powered by AWS.
Get started today with Cohesity DataProtect delivered as a Service in AWS Marketplace.
1Preview available