Like death and taxes, ransomware attacks also seem to be inevitable these days. 2021 was a record-breaking year for hackers who wreaked havoc on enterprises and disrupted everyday life with ransomware challenges such as Conti, RangnarLocker, and HelloKitty. Unfortunately, ransomware is not going away and will only continue to worsen in 2022 and beyond. With current world events, the U.S. government’s Cybersecurity and Infrastructure Security Agency (CISA) issued its “Shields-Up” warning and the FBI reiterated ransomware guidance for ransomware readiness and recovery. While these are U.S.-based warnings, they reflect the challenges ALL organizations face across the globe.
So what can enterprise IT and security teams do to prepare themselves for the inevitable? Proactive prevention is the best defense according to the FBI, as outlined in this “Ransomware Prevention and Response for CISOs” document. FBI guidelines to defend against ransomware include these 10 recommendations, many of which highlight the importance of maintaining an isolated backup copy of data inaccessible from the primary location where the data resides.
Data isolation is not new and many organizations have made it a part of their 3-2-1 backup and recovery strategy—three copies of data, on two different media, with one of them in an off-site environment. Traditionally, data was isolated on magnetic tapes, a.k.a. ‘air gapping’, and then brought back onsite in case of a data disaster. While this approach provides excellent security, recovery is often time-consuming, leading to missed SLAs that are simply unacceptable in light of modern business continuity demands.
To stay agile while protecting data, enterprises are updating their 3-2-1 strategy to improve upon the recovery times afforded by magnetic tape solutions. They are looking to keep tertiary copies of data behind a virtual air gap with physical and network isolation. In some cases this has led to the construction of ‘DIY’ data vaults where IT teams deploy parallel infrastructure to maintain an isolated copy of their data. This approach overcomes the SLA issues faced with the traditional magnetic tape-based air gapping but can quickly become complex and costly to maintain—not a viable option for many enterprises who already have stretched IT teams and tight budgets. Perhaps it’s no surprise then that a recent ESG report1 revealed only 30% of organizations surveyed had deployed an air gap/virtual air gap solution.
Modern Air Gap for the Cloud Era
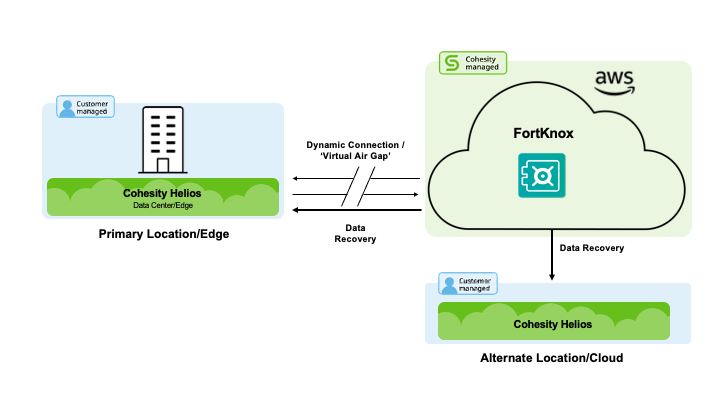
At Cohesity, we help our customers eliminate the complexity and costs of self-managed data isolation techniques with Cohesity FortKnox—our upcoming data isolation and recovery as a service offering. FortKnox is designed to power a modern 3-2-1 backup strategy that effectively balances organizations’ security and agility priorities, enabling them to meet stringent backup and recovery SLAs as well as regulatory and increasingly, cyber insurance requirements. FortKnox improves cyber resiliency with an immutable copy of data in a Cohesity-managed cloud vault via a virtual air gap. This data can be quickly and easily recovered back to source or an alternate location in case of a data disaster. FortKnox provides an additional layer of protection against ransomware and other cybersecurity threats while dramatically simplifying operations and lowering costs, preparing organizations to recover confidently from attacks.
Ensuring Peace of Mind with Comprehensive Data Security
At the core of FortKnox is a multilayered defense-in-depth strategy that goes beyond zero trust to ensure that the vaulted copy of data is the gold standard that they can fall back on in case of a cybersecurity attack. This is achieved through physical, network, and operational isolation that ensures that the vault data and policies are inaccessible to both external and internal bad actors, limiting data exfiltration vectors. Here are some of the ways that FortKnox keeps data safe:
- Virtual air gap through a secure and temporary network connection that is cut off once the data has been vaulted
- Tamper resistance via immutability, WORM, data-at-rest and data-in-flight encryption, AWS Object Lock to prevent changes in retention policy, and separate workflows for vaulting and recovering data
- Access controls through RBAC, MFA to prevent unauthorized access of vault data, as well as quorum that requires at least two authorized personnel to approve critical actions
- Anomaly detection through Cohesity Helios’ machine learning intelligence, which could indicate a possible ransomware attack
- Operational isolation through Cohesity or customer-managed KMS to prevent authorized users who have access to the backup cluster from accessing or restoring vault data
Simplifying Operations and Lowering Costs with as a Service Consumption
Organizations today are faced with severe skills shortages1 and are looking for trusted partners to rely on to share the responsibility of securing their data. FortKnox provides a cloud solution for data isolation that eliminates the complexity of shuttling tapes offsite or maintaining a DIY data vault. Here are some of the ways that FortKnox makes life easier for IT teams:
- SaaS solution that’s as simple as connect, vault, and recover
- Single solution to vault data for a variety of data sources including virtual machines, databases, files, and objects
- Self-service data vaulting and recovery with customizable protection policies
- Centralized user interface to monitor global data vaults
- Reduced costs by moving from CapEx model to a predictable pay-as-you-go consumption model
Ensuring Business Continuity with Confident Recovery
When a ransomware attack strikes, every second counts and teams can rely on FortKnox to recover critical data quickly and easily to a location of their choice. ESG research reveals that organizations focus on ransomware prevention but few are confident that they can recover their data in a timely fashion1. FortKnox helps improve speed of recovery and meet stringent recovery SLAs through:
- Advanced machine learning-based algorithm helps identify a clean copy of data for rapid recovery
- Quick recovery back to source or alternate location, including the public cloud
- Ability to recover specific files and objects without having to restore whole volumes unlike traditional data vaults
How Cohesity Helps You Improve Cyber Resiliency
Ransomware protection and recovery requires a multipronged approach and Cohesity helps our customers on this journey with a range of solutions that support multiple use cases and varied data sources in flexible consumption models to suit individual business priorities. Cohesity FortKnox and Cohesity DataProtect, together contribute to Cohesity’s Threat Defense data security architecture and provide IT teams a formidable insurance policy against ransomware.
This multilayered architecture is continually being enhanced to help customers stay a step ahead of cybercriminals. It brings together a range of products, services, and capabilities from Cohesity and ecosystem partners to help customers identify threats via AI and ML, protect their data, and rapidly recover in the event of a cyberattack. The table below shows how Cohesity can help organizations implement some of the previously mentioned FBI recommendations to protect against ransomware.
| Capability | FBI Guidance | Cohesity Solution |
| Backup and recovery | Back-up critical data offline | Available today via DataProtect and DataProtect as a Service |
| Data isolation | Ensure copies of critical data are in the cloud or on an external hard drive or storage device. This information should not be accessible from the compromised network. | Cohesity supports customer choice through many options:
|
| Data resiliency | Secure backups and ensure data is not accessible for modification or deletion from the system where the data resides. | The combination of Cohesity’s immutable snapshots, WORM (DataLock), and AWS Object Lock protects data from being accidentally or maliciously overwritten, modified or deleted. |
Cohesity FortKnox is currently in preview and will be available globally from Cohesity and its partner ecosystem in Q3 FY 2022, as a subscription-based SaaS offering. Register here to get access to FortKnox when it becomes Generally Available (GA).
To learn more about Cohesity FortKnox, check out this lightboard video, or get a sneak preview in this demo.
1ESG Report, The Long Road Ahead to Ransomware Preparedness, March 2022