For decades, companies have virtualized their IT systems to improve efficiency, gain flexibility, and realize cost savings. Protecting virtual machines is a foundational use case for Cohesity customers.
We’ve long helped enterprises protect their VMware and Nutanix environments, along with other hypervisors. We’re always looking for new ways to invest in our platform and deliver more value to our customers. So when our users asked us to add Red Hat OpenShift Virtualization and Proxmox VE to the list of protected data sources—we did. For many enterprises, these two virtualization technologies are integral to their modern IT estate, allowing development teams to release new code faster and deliver value to their users.
Why we added support for Red Hat OpenShift Virtualization and Proxmox VE
As mentioned, Cohesity has long offered protection for popular hypervisors, as well as other data sources, such as Azure, AWS, and NAS. With market dynamics changing, some IT teams have adopted a dual-vendor strategy. Red Hat OpenShift Virtualization and Proxmox VE have become popular choices for many organizations. Now, organizations can use Cohesity Data Cloud to continue to improve cyber resilience for these workloads with immutable backups, zero-trust principles, and more.
How it works
The process looks slightly different depending on whether you’re protecting Red Hat OpenShift Virtualization or Proxmox VE. Administrators can now add both data sources to their deployments within Cohesity Data Cloud, with no additional configuration required.
Red Hat OpenShift Virtualization
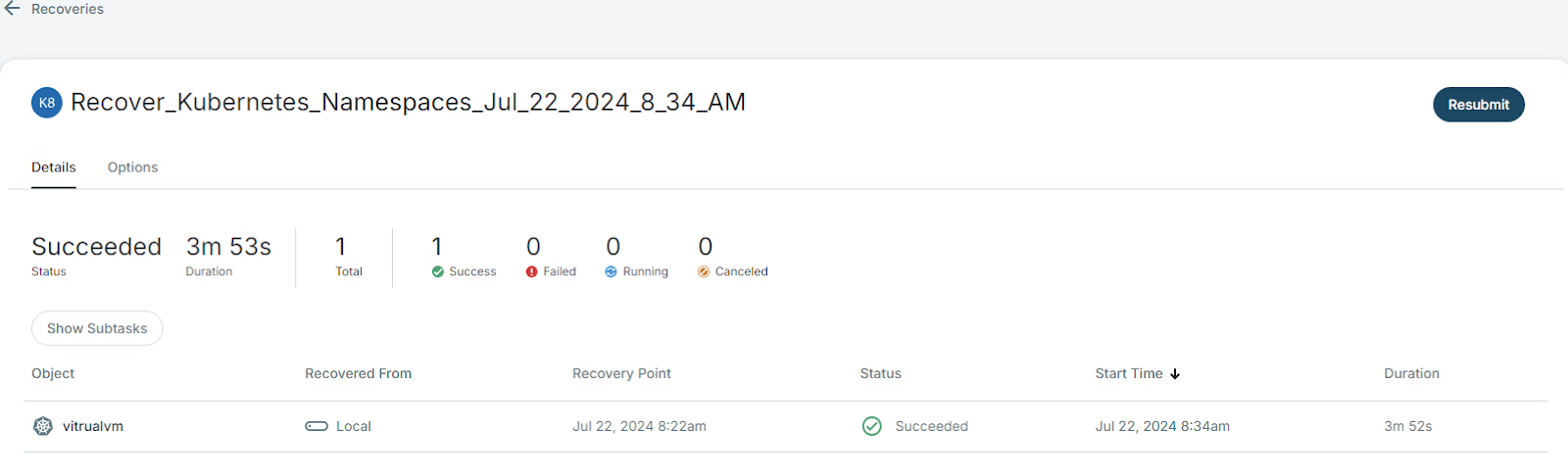
There are two ways to protect and recover OpenShift Virtualization workloads. First, the OpenShift/Kubernetes approach. This integration is something we are currently building out and have tested successfully. We look forward to delivering this to customers in the coming months. Catch a sneak peek from the screenshots below. With it, you can protect OpenShift containers and virtual machines with their underlying storage by registering your OpenShift instance with Cohesity. In such a configuration, Cohesity will communicate with OpenShift and deploy its data mover pods to protect data securely. With a single registration, you can protect containers and virtual machines with granular control over the components of OpenShift like persistent volume claims (PVCs), namespaces, and the like.
The second, which is available today, is an agent-based approach. In this scenario, a customer can install Cohesity’s agents that match the VM’s operating system and protect file data as usual. To recover the data, administrators simply select the files and restore them. If the target is a new or an alternate VM, once an agent instance has been brought online, recovery can be accomplished.
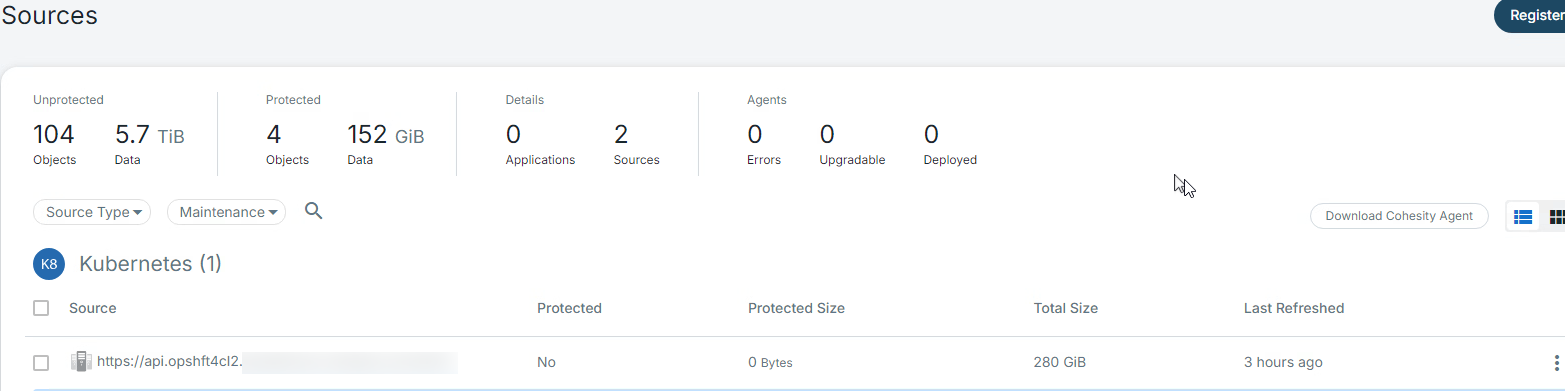
Registration of Source
Figure A shows the registration of the source.
Protection
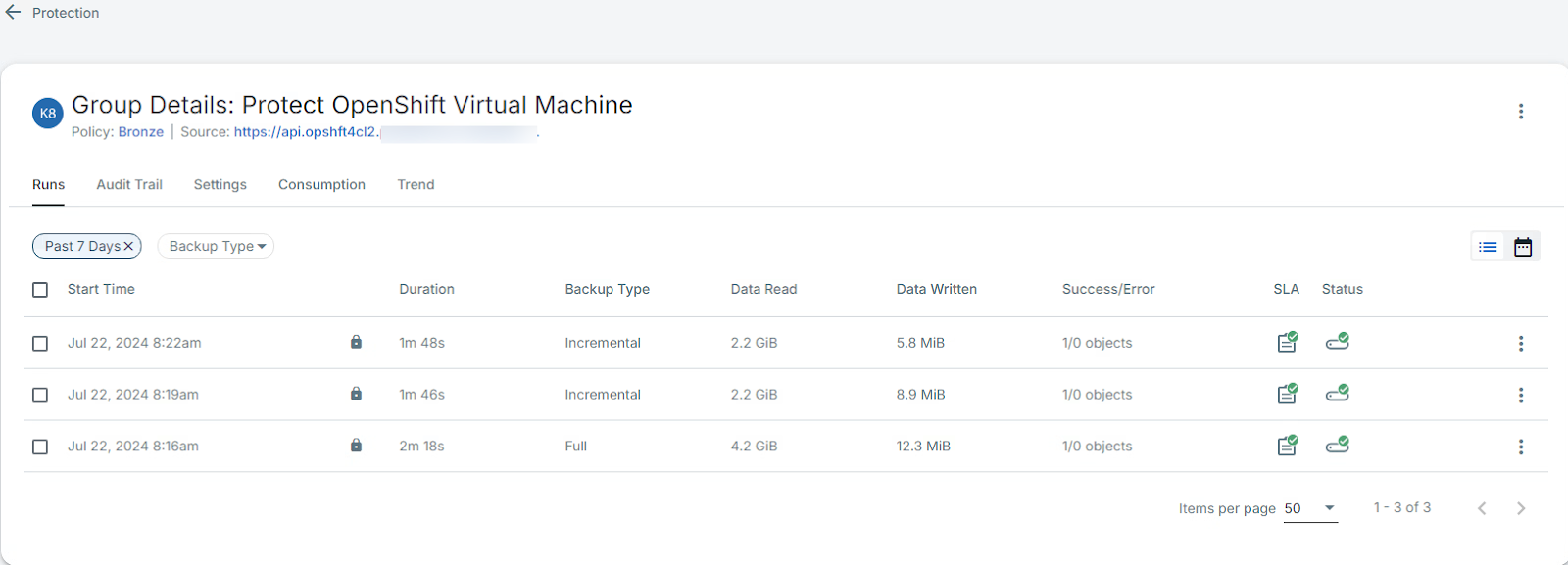
Customers can then use a policy-based approach to protect selected objects in their OpenShift environments, just as with other data sources.
Figure B shows the protection group run history.
Recovery
VM recovery follows the same workflow that Cohesity users are familiar with.
Proxmox VE
Depending on how you use Cohesity, there are two ways to protect Proxmox instances. The first utilizes Cohesity storage as a simple target repository for backup files. The first uses the native backup capabilities provided by Proxmox to protect the VMs. In this scenario, users would use DataProtect to create a Network File System (NFS) view on the Cohesity cluster, add this view as an NFS storage pool in Proxmox, and then use the native backup tool to save VMs of interest to it. The view can be protected for the customer’s duration of choice, providing the benefit of immutability.
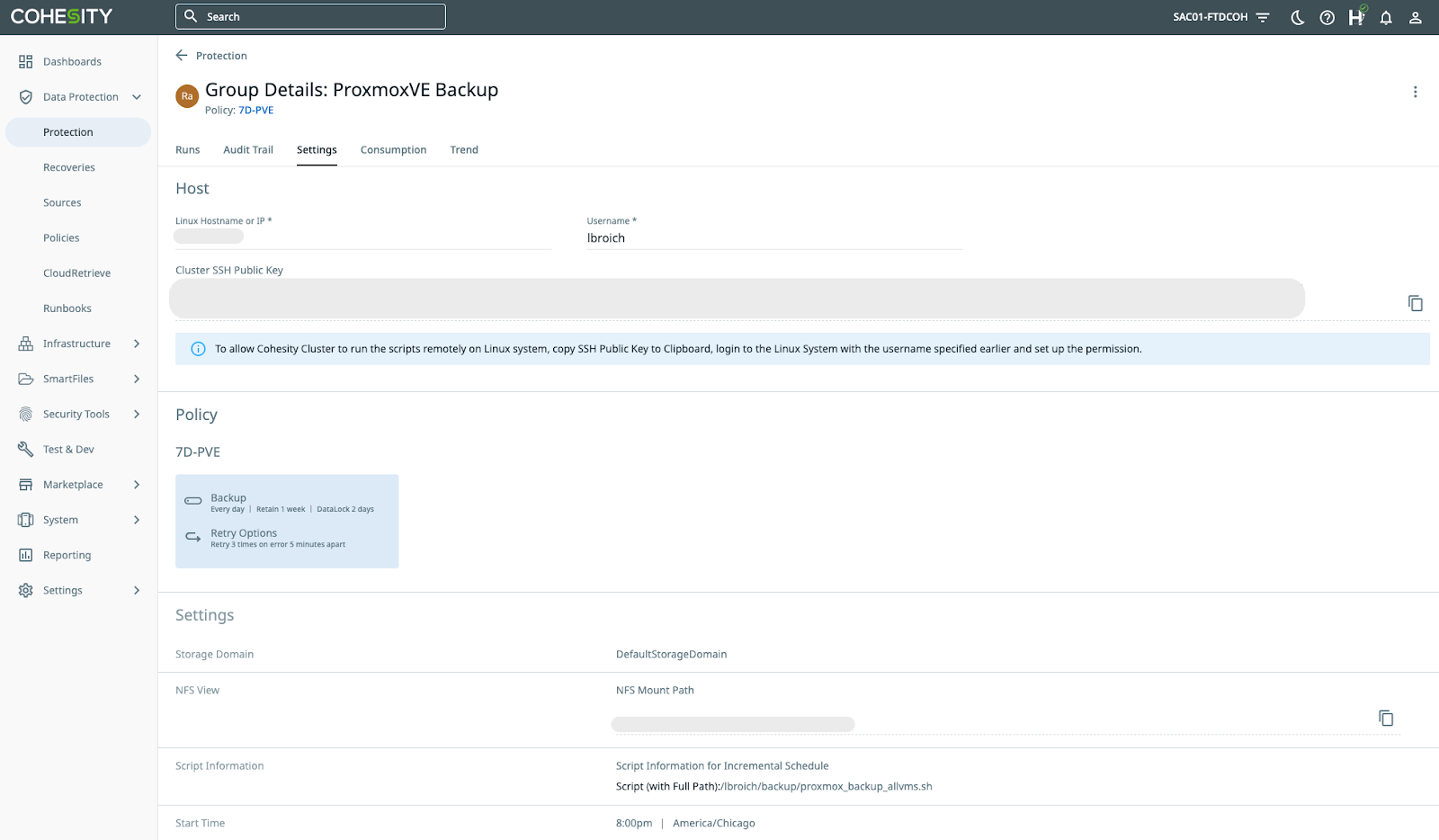
In the second method, users can use Cohesity’s policy-driven architecture to schedule and orchestrate the backups using Remote Adapter. In this approach, the backup commands can be provided in a script on the Proxmox host to invoke protection. The Remote Adapter ensures that the view is protected and immutable.
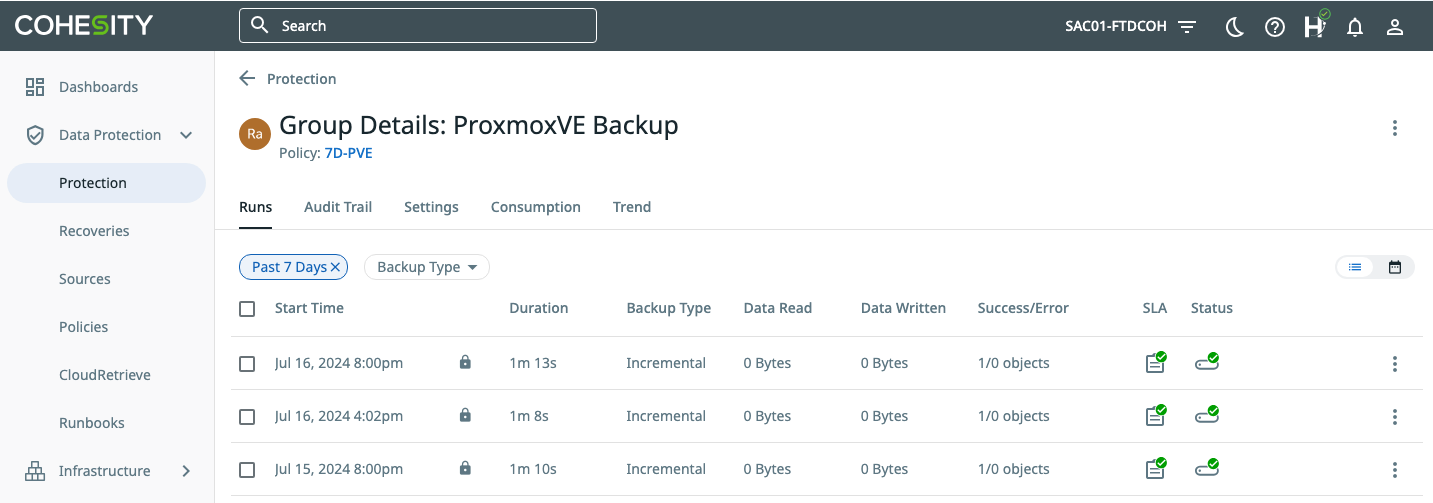
Figure D shows the protection group run history.
Both methods produce immutable backups on Cohesity Data Cloud that can be restored using Proxmox native workflows.
Figure E shows the protection group configuration.
How we’re protecting virtual machines and more
Our platform, Cohesity Data Cloud, makes it all possible by allowing organizations to protect VMs—and other cloud, SaaS, and on-prem workloads—at scale. IT teams can manage and secure their entire data estate using the following capabilities:
- A single UI simplifies data management and enables protection at scale.
- Instant cyber recovery, instant access and unlimited clones that speed up recovery.
- Immutable snapshots, encryption, WORM, RBAC, MFA, and quorum to improve your security posture.
- AI–powered operational and business insights to drive efficiency, accelerate the detection of potential anomalies, and make smarter decisions.
Elevate your cyber recovery capabilities with Cohesity
As your business grows, you need a partner who will grow with you. Our platform was built on zero trust principles, including immutability, encryption, MFA, and it was designed to scale. As the needs of our customers and the market have changed, so have we, adding support for additional workloads, advanced security features, and even launching the industry’s first Data Security Alliance. Extending protection for Red Hat OpenShift Virtualization and Proxmox is just one of the many recent additions to our platform that ensure modern protection for your enterprise. To learn more, get qualified to start a free trial.