Cyber resiliency remains elusive for most organizations, especially in the context of ransomware attacks. According to an ESG survey, just 14% of organizations recover all their data after a ransomware attack—even after paying the ransom. In the Hiscox “Cyber Readiness Report 2022”, respondents reported a rise in both cyber and ransomware attacks and the cost of cyber incidents.
What’s needed in a data security and management platform
Organizations need a platform that combines data security and data management in a single unified environment that frees data from silos, securely, and makes it available and accessible in support of the business. With this platform, organizations can safely back up and restore data in case of a cyber incident with speed and confidence.
For cyber resilience, the data security and management platform needs to:
1) Implement a backup and recovery solution that prevents tampering with the data and platform
The foundation for data resilience is the immutability of backup data and the security of the backup platform. Immutability helps prevent threat actors from changing/tampering/deleting backup data. And for the backup platform, only authorized staff can change settings and backup schedules. With these capabilities, organizations can confidently rely on the integrity of the backup data for recovery.
2) Support and amplify existing cyber defenses
While cybersecurity defenses continue to improve and adjust to threat actor tactics, they may be compromised by sophisticated zero-day attacks. And when cybersecurity defenses detect attacks, they have little control over data resilience solutions to implement recovery after incident response teams have investigated and contained threats.
In support of cybersecurity defenses, data resilience solutions have the unique ability to analyze all mission-critical data during routine backup processes. With the platform leveraging ML, changes in data that can indicate an emerging attack can be identified as anomalies and then routed to incident response teams. This means integrating into security operation centers (SOCs) that are powered by SIEM and SOAR solutions. Playbooks then guide the response to the data anomalies including the recovery of data and systems.
3) Provide confident and rapid recovery measured in hours vs days and weeks
Confident and rapid recovery provides organizations with reliable and fast restoration of critical business processes and data to meet their demanding recovery time objectives (RTOs). First, based on ML, platforms should provide organizations with the last known good recovery point and powerful search so that organizations can ascertain the status of specific data instances. Next, they need to validate that the recovery data does not reintroduce vulnerabilities and threats by scanning for known vulnerabilities and indicators of compromise (IOCs) provided by threat intelligence.
Finally, highly scalable architecture fed by complete backups of all critical data and processes is needed, so that organizations can recover hundreds of VMs, files, or any size database instantly. This process allows IT staff to meet business SLAs while saving time and resources.
Cohesity Data Cloud Release 7.0 key capabilities for cyber resiliency
Adding to Cohesity’s award-winning capabilities, the 7.0 software release of Cohesity Data Cloud provides key capabilities to help organizations achieve their cyber resilience goals:
- Data security hardening
- Hardened access controls to tighten control and management of privileged administrative accounts and protections of access credentials. These controls prevent threat actors from deleting backup data or changing backup schedules which would leave organizations vulnerable to ransomware extortion and ensure access controls can be leveraged when targeted by ransomware and other attacks.
- Cohesity Data Cloud Release 7.0 features these security capabilities to improve data security and cyber resiliency:
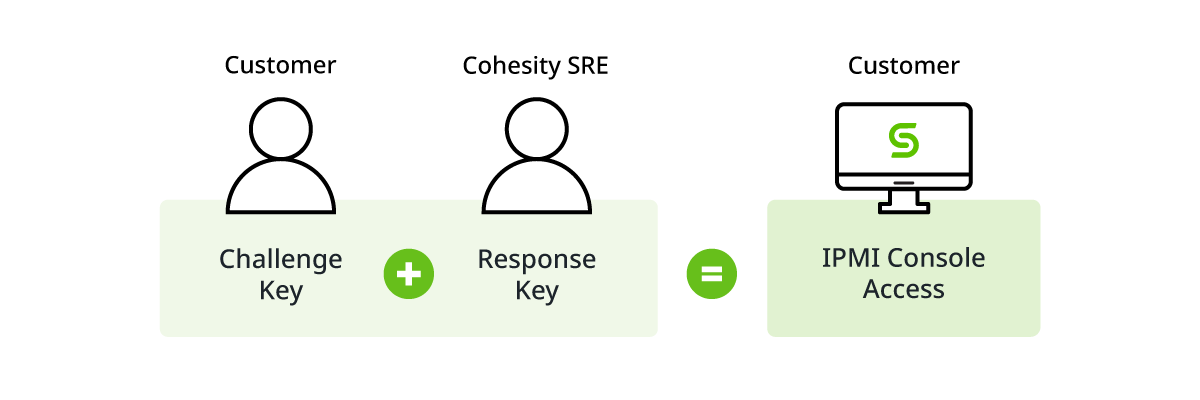
- Split Key Access for IPMI Access requires the customer and Cohesity to each provide a key for the access of the IPMI console. This console allows granular control of server settings and could be used maliciously by threat actors. With each party needing to provide a part of the split key, rogue or unauthorized users can not leverage the IPMI console as an attack vector.
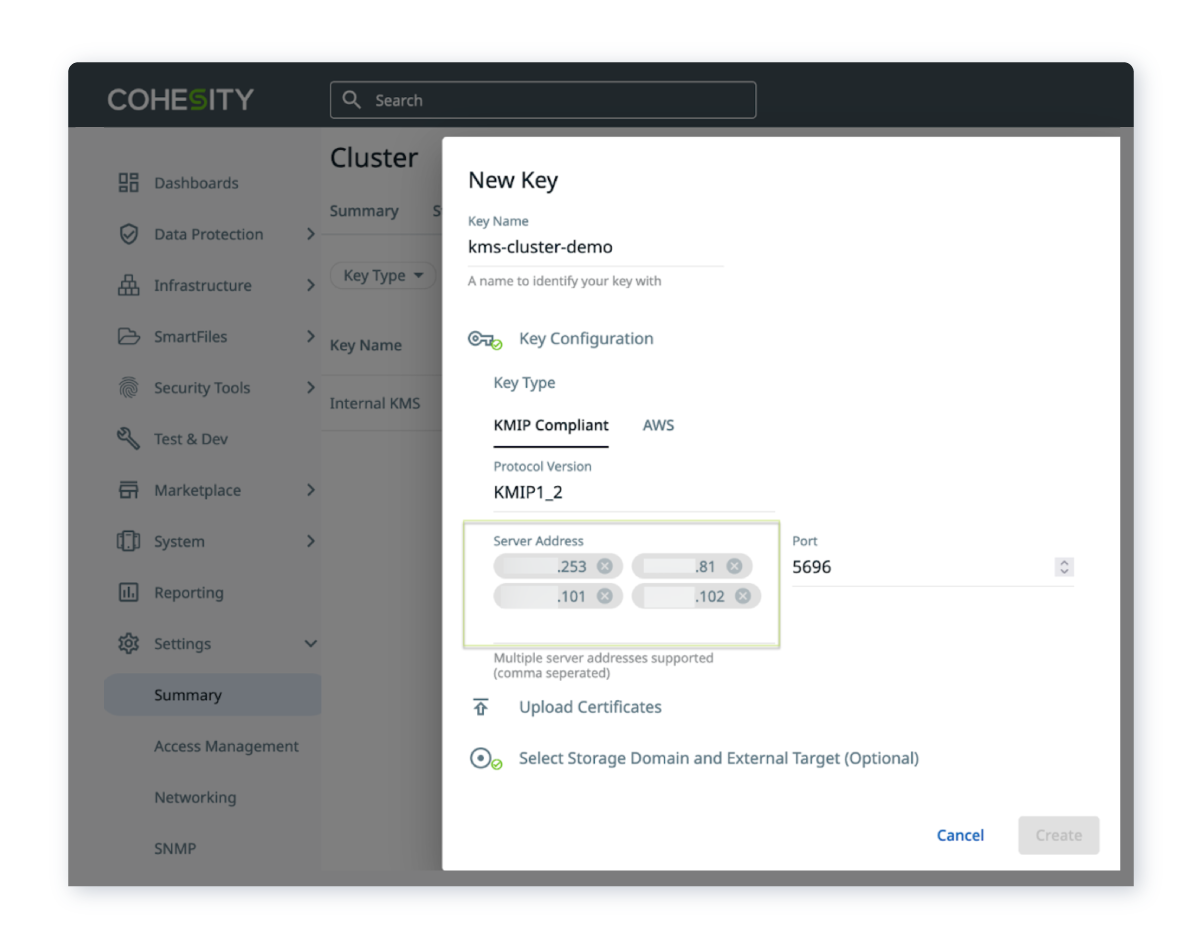
- Key Management System (KMS) Auto-Failover provides failover for the key management systems that provide the credentials for authorized access to the platform users and administrators. If an attack occurs, it is critical to have the KMS operational to ensure rapid recovery.
- Split Key Access for IPMI Access requires the customer and Cohesity to each provide a key for the access of the IPMI console. This console allows granular control of server settings and could be used maliciously by threat actors. With each party needing to provide a part of the split key, rogue or unauthorized users can not leverage the IPMI console as an attack vector.
- Extended platform and workload support
- Extended coverage of platforms allows organizations to power their cyber resiliency with the scalability to support the diversity and complexity of global IT.
- Cohesity 7.0 provides these new platform and workload capabilities:
- Cloud Archive and Cloud Archive Direct qualification for organizations to leverage AWS GovCloud as a target data and metadata protection. Along with Cloud Archive support for Azure hot tier storage targets, for all workloads, new platforms supported for on-prem or self-managed including Lenovo SR645, HPE DL360 and DL380, Cisco UCS C220M6 AFC, and C240 M6, and Dell 740XD.
- Workload capabilities include expanded OS support for Oracle 21c, and Oracle on Solaris and continued database support enhancements for MongoDB with point-in-time database level recovery, SAP Oracle running in Windows environments, MongoDB on GCP, and more.
- Fortifying security and resilience of files and objects
- As data volume rapidly grows, simplicity and efficiency in managing, protecting, and recovering unstructured data allow faster recovery from outages and malicious attacks.
- Cohesity Data Cloud Release 7.0 features these file and object features:
- Enhanced granularity of file and folder restores enable precision recovery of impacted data, while preserving good data.
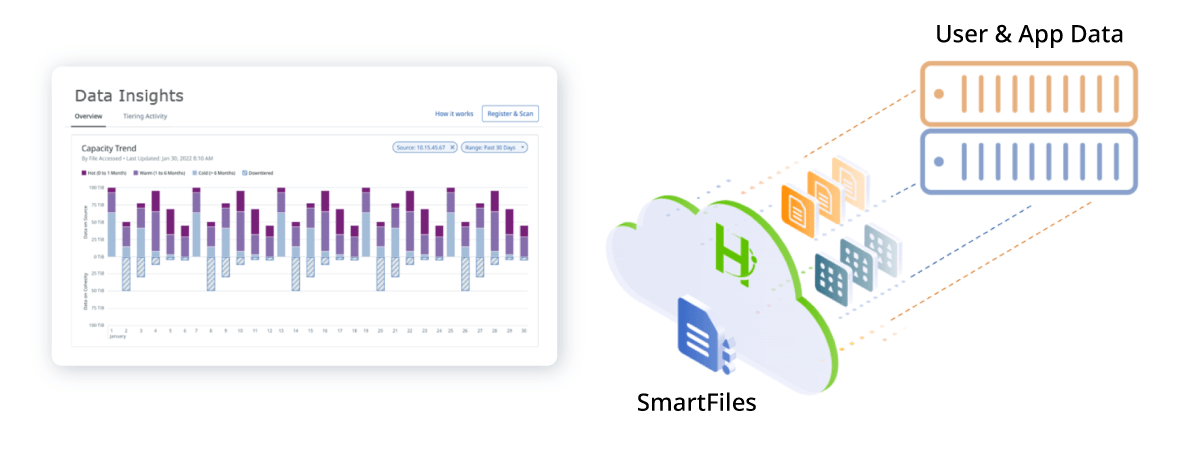
- Enhanced lifecycle management for file and object data provides automated tiering of data from 3rd party systems to Cohesity SmartFiles to optimize costs and satisfy data security, compliance, and governance requirements.
- Custom policies protect critical object data from unauthorized access and attacks by providing overarching control of access by users. Object lock enhancements streamline the configuration of immutability, retention, and legal hold.
- New data analytics capabilities enable deeper insights and visualizations for user and application data consumption, data temperature, client connections, data reduction statistics, and more.
- As data volume rapidly grows, simplicity and efficiency in managing, protecting, and recovering unstructured data allow faster recovery from outages and malicious attacks.
As noted in the Forrester Wave “Data Resilience Solution Suites, Q4 2022”, “Today’s enterprises are transitioning to a hybrid cloud world. This means that they must not only back up data in diverse infrastructure environments but also secure that data (and the backup infrastructure) from cyberthreats, recover from failure faster, navigate shared-responsibility models for hosted services, and address data privacy and sovereignty concerns—all while expanding automation, increasing self-service capabilities, and streamlining management of backup-and-restore capabilities.”
Cohesity 7.0 provides key capabilities for cyber resilience by supporting the need for reliable and confident recovery and for integrated cybersecurity and data security and management. Contact your Cohesity account representative to learn more.
To learn more about Cohesity Data Cloud Release 7.0, read our press release.