Security teams face an uphill battle in defending against today’s cyberattacks. In 2023, attackers adopted more effective methods, such as credential harvesting and vulnerability exploitation, to infiltrate systems while evading detection. Their speed is also a growing concern, with breakout times shrinking from 84 minutes in 2022 to just 62 minutes in 2023. Additionally, adversaries constantly evolve their methods, experimenting with innovative malware delivery techniques and using AI to outmaneuver traditional defenses. These alarming trends highlight the need for more effective and efficient threat detection and incident response strategies.
Today, with the general availability of the Cohesity Data Cloud integration with CrowdStrike Falcon® Adversary Intelligence, we deliver enhanced threat hunting and response efficiency to help level the field using your secondary data estate. Our latest collaboration with CrowdStrike, one of our inaugural Data Security Alliance partners, allows customers to bring their own (BYO) cyber threat intelligence. The addition of CrowdStrike’s world-class threat intelligence feeds, which tracks over 250 adversaries—exposing their activity, tools, and tradecraft—while incorporating indicators of compromise (IOCs), allows customers to detect the latest threats with higher fidelity and accuracy and enhance the effectiveness and efficiency of their response activities. Our latest integration with CrowdStrike can work alongside our existing integration with CrowdStrike® Falcon LogScale™, which helps security teams detect more threats faster and investigate with greater intelligence.
Four reasons to adopt the Cohesity Data Cloud integration with CrowdStrike Falcon Adversary Intelligence
Attackers always have the first-mover advantage, catching defenders by surprise and forcing them into a reactive position. This leads to a race against time to confirm the attack, determine the scope of impact, and contain the threat.
Using your secondary data estate on Cohesity—combined with industry-leading solutions like CrowdStrike Falcon Adversary Intelligence—can help minimize some of the attackers’ advantages. Here’s how:
- Integrating threat intelligence feeds created from observations on your own endpoints produces higher-fidelity, more accurate alerts, allowing your team to focus on the specific threats your organization has encountered. Falcon Adversary Intelligence delivers custom IOCs derived from the automated analysis of threats that reached your endpoints.
- Our approach allows you to run threat hunts on backup copies—letting you investigate stealthily and out of band from where the attacker has persistence. Threat hunting using Cohesity adds some significant capabilities beyond what can be achieved by solely relying on endpoint detection solutions. Detection occurs on your secondary data rather than the host itself, meaning Cohesity’s ability to discover IOCs is not impacted by incident containment activities that may isolate hosts and networks. Additionally, evasion techniques used by adversaries to render endpoint solutions ineffective will not work against Cohesity’s detection approach. Essentially, threat hunting using Cohesity, combined with the latest threat insights from CrowdStrike, enhances the effectiveness and efficiency of your response activities.
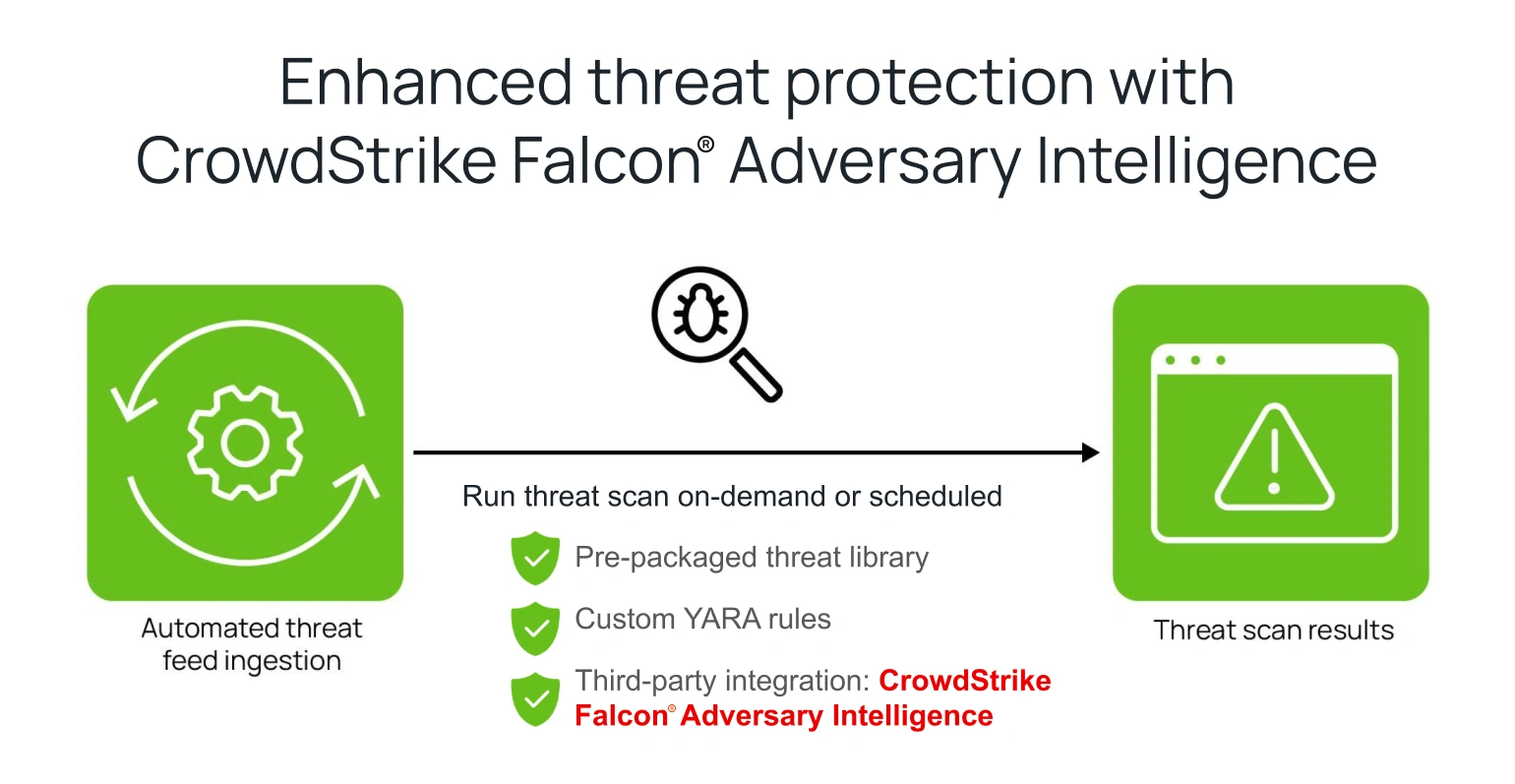
- Cohesity’s robust threat protection framework also gives you the flexibility to augment capabilities through custom rules as the situation unfolds, providing the agility needed to successfully contain and evict an active threat. Our scalable threat protection framework allows you to scan your secondary data for threats effectively by integrating default threat feeds, custom Yet Another Recursive Acronym (YARA) rules, and third-party sources like CrowdStrike in a single scan.
- The addition of CrowdStrike’s world-class threat intelligence feeds allows you to better detect the latest IOCs before restoration— minimizing the risk of re-attack while streamlining the response and recovery process.
How to get started
If attackers use more powerful tools, the question becomes, “How do I get more out of my tools to compete?” Fortunately, integrating powerful tools like Cohesity and CrowdStrike can be accomplished in just minutes, simply by providing the necessary account and API details.
The result is a faster transfer of information between the two platforms, resulting in higher fidelity of alerts and a deeper understanding of what is happening in an environment.
Ideally, it means intruders are identified and evicted quickly before they can impact the environment. In situations where an attack is successfully launched, a tighter integration like this can help the organization navigate the response more confidently and with less risk.
Watch this video to see how to easily deploy and use this integration in your environment.
Learn more about integrating the Cohesity Data Cloud with CrowdStrike Falcon Adversary Intelligence
Check out the details and documentation on the Cohesity Marketplace to dive deeper into the integration.
To learn more about the latest global threat trends and our latest collaboration with CrowdStrike to strengthen threat hunting and response efficiency, visit cohesity.com/crowdstrike.