With ransomware impacting organizations of all sizes, disrupting critical infrastructure and rocking global and national economies, some prominent political leaders deem it a national security threat. All organizations are now being strongly encouraged to prepare for a potential cyber attack.
Data backup and recovery have become a top priority when implementing a comprehensive defense against cyber attacks. As threat actors become more sophisticated, they are targeting an organization’s backup before encrypting the data in the production environment to raise the likelihood of receiving payouts.
To help organizations combat these types of threats and gain deep visibility, Cisco and Cohesity have integrated Cisco SecureX and Cohesity Helios to automate detection, response, and recovery in the face of ransomware attacks. This is the first data protection solution integrated with SecureX, ensuring data-level security in addition to securing networks, clouds, endpoints, and applications.
Cybercriminals Are Going After Your Backup Data
Why do attackers often go after the backup first? The answer is simple. If cybercriminals destroy your backup and then encrypt the data in your production environment, you cannot recover without the encryption keys. In other words, if they wipe out your backup, the only way to recover is to pay the ransom for the keys to unencrypt your production environment.
Therefore, in addition to securing the network, cloud, endpoints, applications, and perimeter as tightly as possible, it is crucial that your organization also focus on data protection–including the protection of backups–as it is your last line of defense.
Cybercriminals Have Become Bold
Cybercriminals are increasingly launching more sophisticated attacks. For example, during the SolarWinds hack in early 2020, cybercriminals, perhaps supported by a nation state, secretly integrated malicious code into SolarWinds’ software source code. The malicious code was then unwittingly sent to their 33,000 customers through regular software updates, creating backdoors into customers’ internal systems, including U.S. Government systems. Eventually, the cybercriminals used those backdoors to install more malware, enabling them to spy on SolarWinds’ customers. As another example, we are still trying to comprehend the scope of the Kaseya VSA supply-chain ransomware attack.
U.S. hospitals and healthcare providers have become the prime targets of cybercriminals spreading the Ryuk ransomware for financial gain. One such institution, Sky Lakes Medical Center, had to take offline 650 servers and 150 critical applications used to run the hospital and treat patients. An employee at the medical center had clicked an innocent-looking link to a Google Docs file, which was a disguised phishing email. That email dropped the Ryuk ransomware payload into the medical center’s network and systems.
Organizations Need to Prioritize Data Protection
Unfortunately, with the traditional approach to data protection, IT operations teams face many obstacles to strengthening their organization’s data security, such as:
- Complexity—Incident investigation through multiple consoles without a way to confidently estimate recovery SLAs in response to a ransomware attack increases risk to the business.
- Siloed visibility—Lack of unified visibility into the data when ransomware strikes, slows the ability to quickly identify and remediate the threat
- Slow remediation—Manual coordination among multiple teams across operational silos results in slow response and recovery. This practice is also exhausting and stressful, leading to cybersecurity fatigue and burnout.
The case of Sky Lakes Medical Center demonstrates the importance of recovery speed. Every minute its servers and applications were offline was another minute the healthcare provider could not treat its patients. Thanks to Helios, a next-generation data management platform, Sky Lakes Medical Center rapidly recovered data and workloads at scale without paying a penny of the ransom, while also potentially saving lives.
Simplify the Protection of Your infrastructure with SecureX
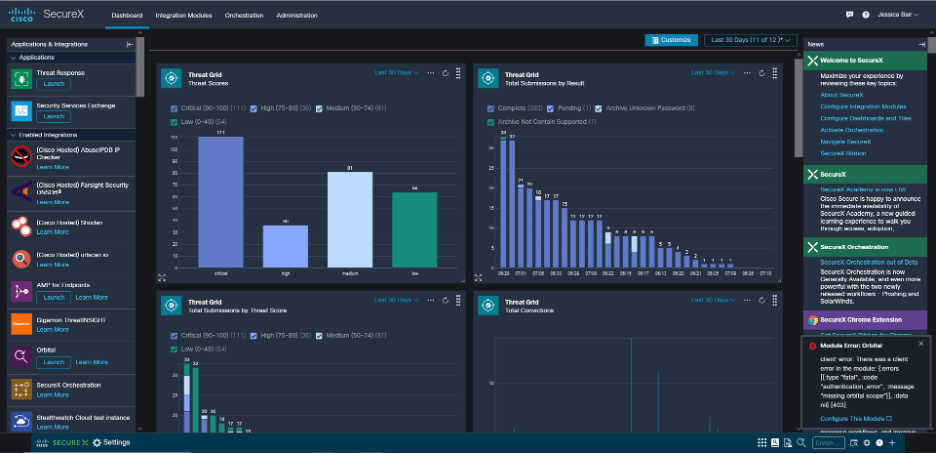
To strengthen your security against cybersecurity threats, SecureX connects the breadth of the Cisco Secure portfolio to your infrastructure, including your networks, endpoints, and applications running both on premises and in the cloud. SecureX is a built-in, cloud-native platform, which provides a simplified, singular view that unifies visibility, reduces dwell time, and streamlines human-powered tasks through automation (Figure 1).
Figure 1 SecureX Dashboard
Protect Data and Backups Through Cohesity DataProtect
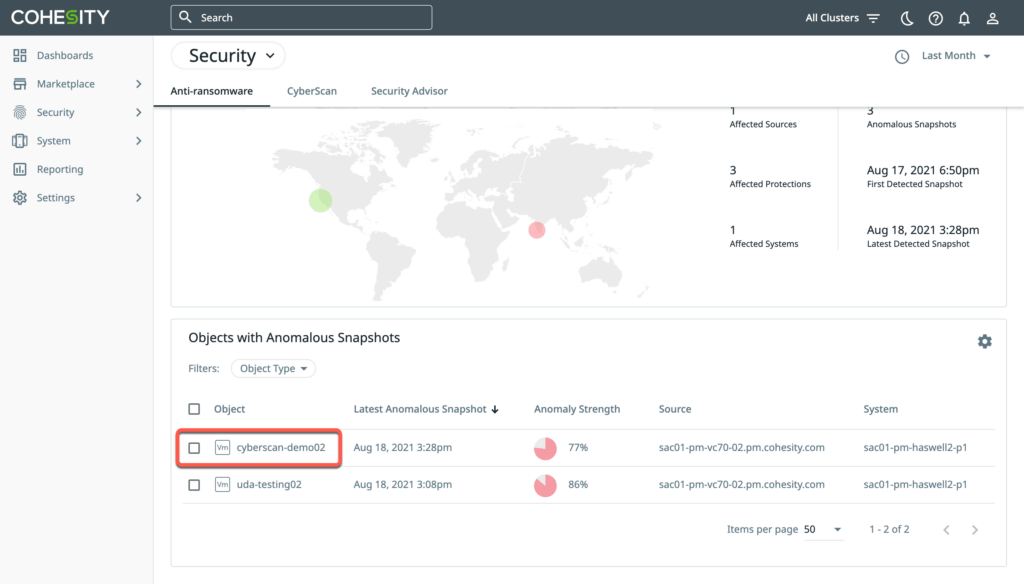
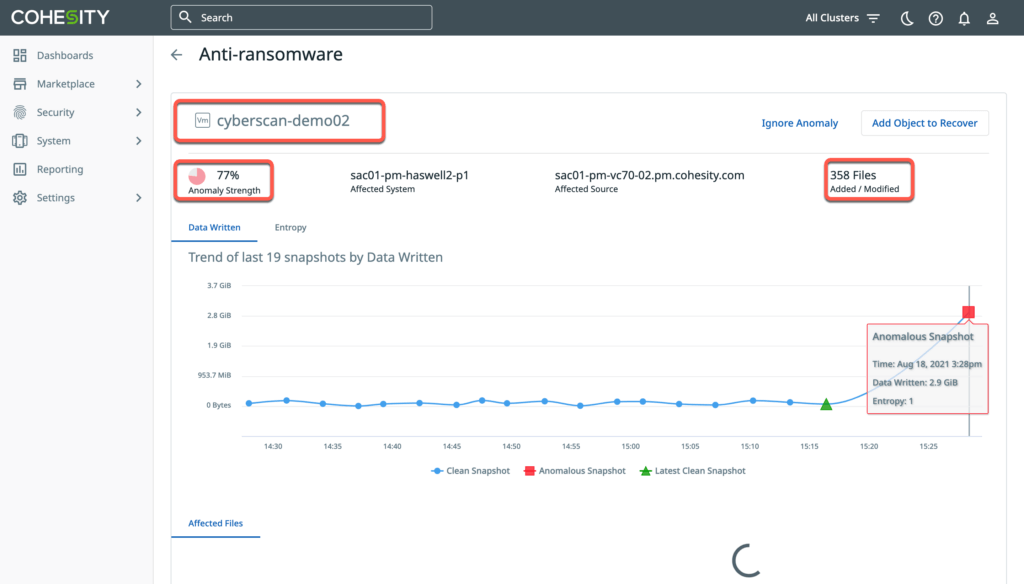
An organization’s data is a uniquely valuable asset that must be protected and available at all times. DataProtect, a backup and recovery service that runs atop Helios, simplifies how organizations manage and protect their data. Its comprehensive anti-ransomware capabilities protect, detect, and most importantly, help organizations recover quickly to reduce downtime, minimize loss, and ensure business continuity (Figures 2 and 3).
Figure 2 Helios Security Dashboard
Figure 3 Helios Anti-Ransomware Visual
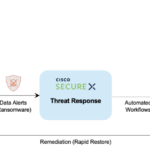
SecureX and Helios API Integration
The SecureX platform provides detection and response capabilities to everything on the network, both at the cloud and application level. Data-level security is now available through the integration with Helios. Through an API-level integration, SecOps, ITOps, and NetOps teams all now have the same data security context they need at their fingertips within the SecureX experience for collaboration in countering ransomware threats to backups (Figure 4).
Figure 4 Cohesity Integration with SecureX
Helios allows for automatic scanning of backup data to check for anomalies that indicate potential ransomware and communicate such alerts to SecureX. In addition, you can enable the Private Intelligence dashboard tile in SecureX to show a visual indicator notification when Helios (or other enabled integrations using this feature) register new incidents (Figure 5).
Figure 5 SecureX Dashboard with Cohesity Alerts in Private Intelligence
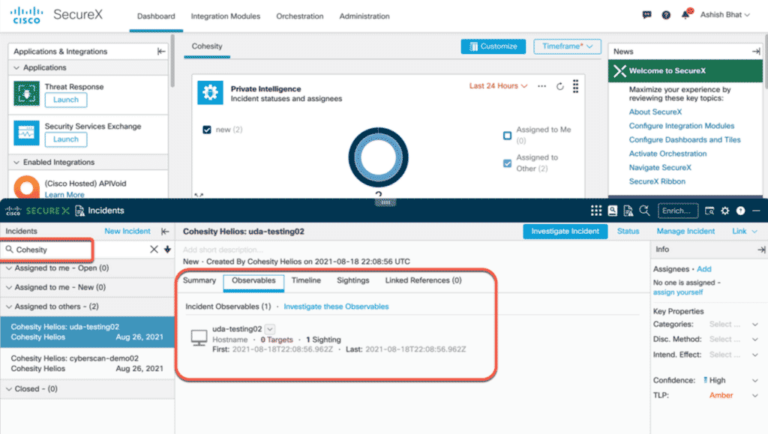
The SecureX incidents show any identified anomalies, along with other signals that may help validate suspicious activity (Figure 6).
Figure 6 SecureX Dashboard with Cohesity Incidents
This capability provides much higher levels of visibility so that a SecOps team can identify, correlate, and address the data security aspects of their infrastructure in addition to protecting networks, endpoints, and applications.
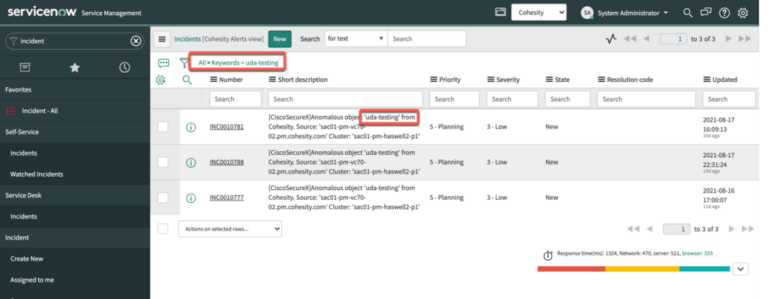
An additional integration with Cohesity ServiceNow through SecureX helps speed incident response, opening a ticket automatically to initiate broader team coordination via workflow in the event of a cybersecurity attack—and orchestrating the initiation of data recovery when needed (Figure 7).
Figure 7 ServiceNow Integration Through SecureX
Cohesity + SecureX = Data Security Simplified
When developing your security posture to include cyber threat defense, it is vital to include a comprehensive focus on protecting your organization’s backup—the last line of defense—and predictable recovery at scale. This focus includes putting in place a security platform that prioritizes data protection with unified visibility and automation to optimize the time and resources enterprises spend to detect, investigate, and remediate ransomware threats.
To learn more, join our webinar and visit cohesity.com/cisco.