When you are in the midst of a cyberattack, the speed of your response matters. Nowadays, the median ransomware variant can encrypt 100,000 files in just 43 minutes. Every second counts as you scramble to minimize the extent of data loss and disruption to business-critical applications.
Cyber resiliency is top-of-mind for Cohesity as we develop our product capabilities, and we’re pleased to announce new adaptive and automated data protection capabilities—designed to help customers significantly reduce their risk of data loss in a cyberattack using real-time threat intelligence sharing and an accelerated threat response approach.
At the earliest signs of ransomware, Cohesity DataProtect will preserve potentially infected virtual machines for future forensic investigation while simultaneously protecting data and workloads in the rest of the environment. As a result, InfoSec teams are intrinsically more proactive in data protection, ensuring they have a quick recovery point in case the threat proves to be real.
This new capability will be available first as an integration between Cohesity DataProtect and Cohesity DataHawk with Cisco Extended Detection and Response (XDR). Our two companies have a long track record of innovation. This forthcoming integration adds to our existing jointly-validated solutions on Cisco UCS that helped over 460 customers improve backup and recovery, disaster recovery, and file and object services. It also builds on a prior integration with Cisco SecureX that helps customers simplify security operations.
Security is a team sport, so you can expect these capabilities to launch with additional Cohesity Data Security Alliance partners.
Now, let’s take a closer look at how the feature is designed to work in the real world.
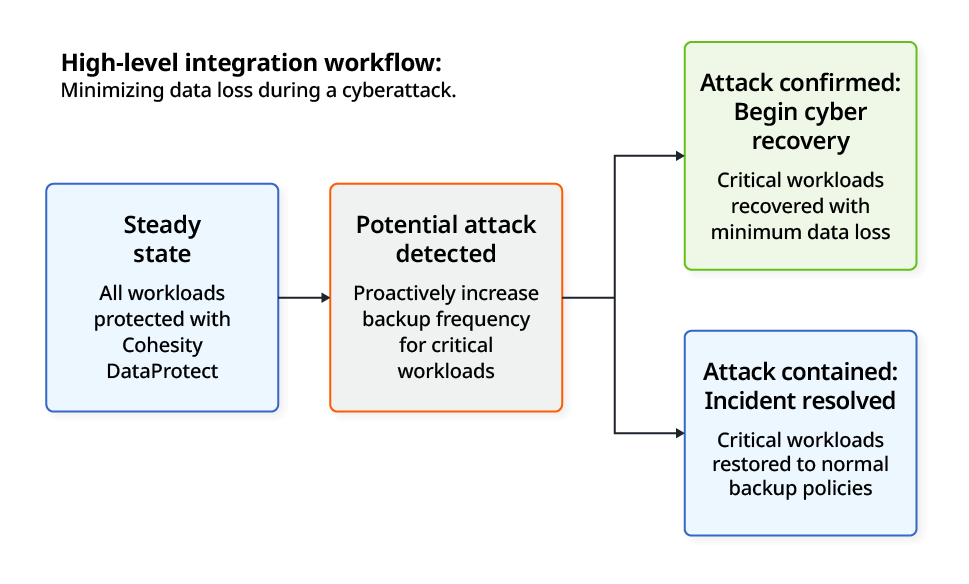
How Cohesity is better together with Cisco XDR
The integration reduces the risk of data loss during an attack by ensuring that the most important workloads are backed up more often when the ambient threat level is high. When the threat level recedes, backup policies are automatically relaxed.
Let’s take a look at a real-world example of a customer environment being attacked with ransomware.
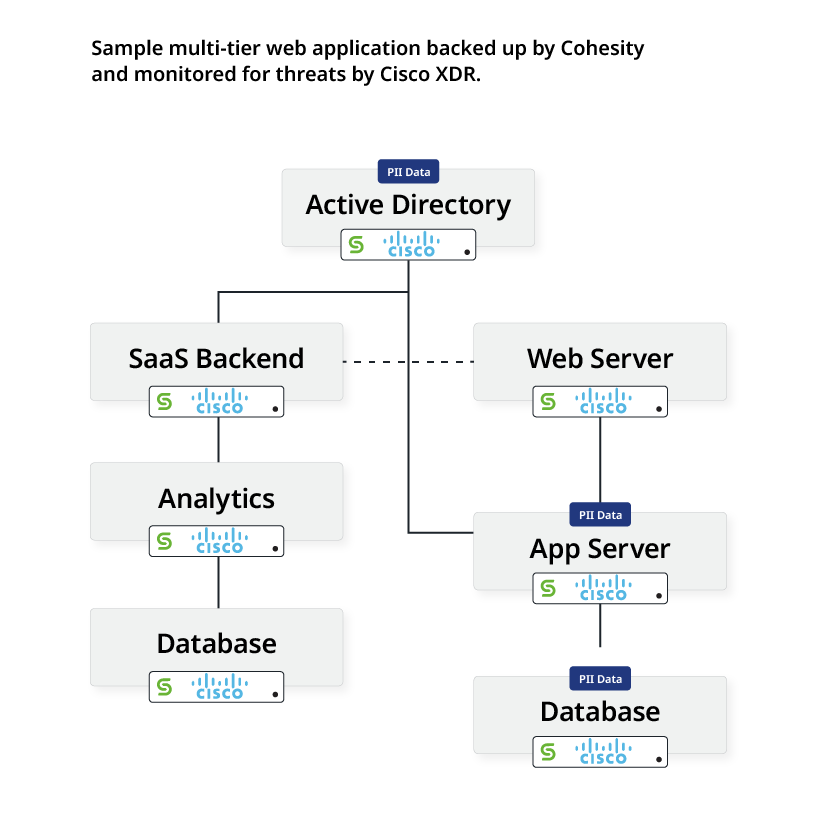
Stage 1: Before the attack
Consider a typical multi-tier web application that is connected to multiple critical workloads, shown below.
Each workload is backed up by Cohesity, and monitored by Cisco XDR for threats. At this stage, Cohesity DataProtect is actively reporting the backup profile for every workload to Cisco XDR. Cohesity also tags critical workloads on which sensitive data was detected by DataHawk Data Classification. Cisco XDR combines this information with the topology information it maintains to create blast radius maps which help determine possible lateral movement paths to critical workloads. During this stage, the backup protection policies designated to workloads determine their respective RPO.
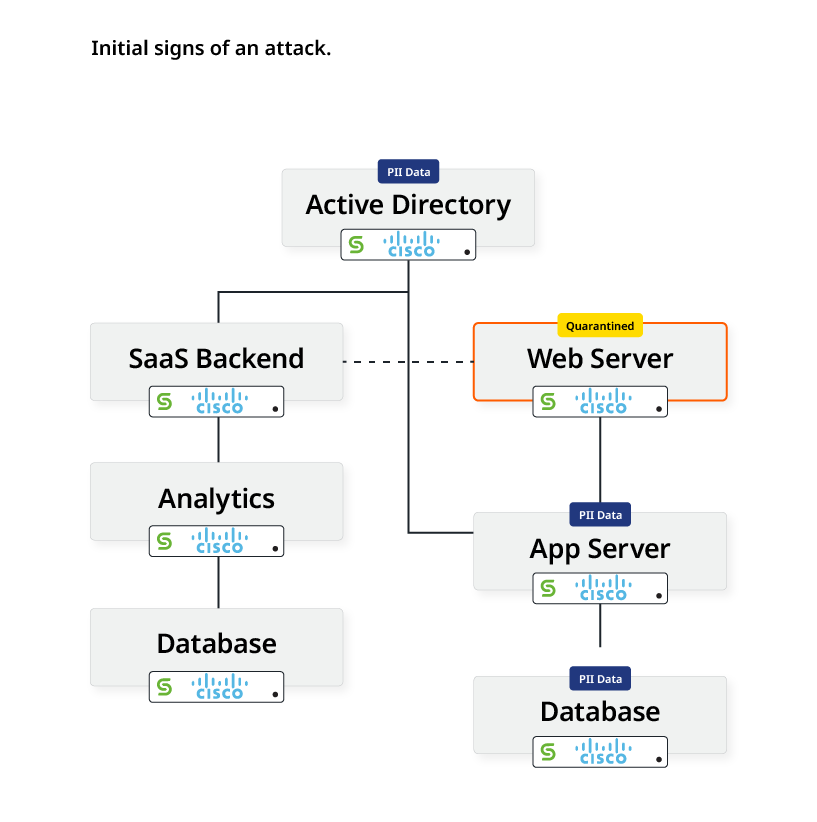
Stage 2: During an attack
Now, let’s say that an attacker compromised the web server shown above by exploiting a vulnerability or another vector. The attacker plants a malicious binary and begins recon to expand the attack.
At this stage, Cisco XDR’s multi-variant threat detection engine detects the new, suspicious activity as a confirmed Indicator of Compromise consistent with a new variant of ransomware. This is a strong signal—the system assigns the malicious binary a 95% likelihood of being a threat.
Now, two things happen.
First, the Cisco XDR ransomware playbook initiates and isolates the web server. Cisco XDR then directs Cohesity DataProtect to take an immediate snapshot of the web server that will be critical for future forensic analysis.
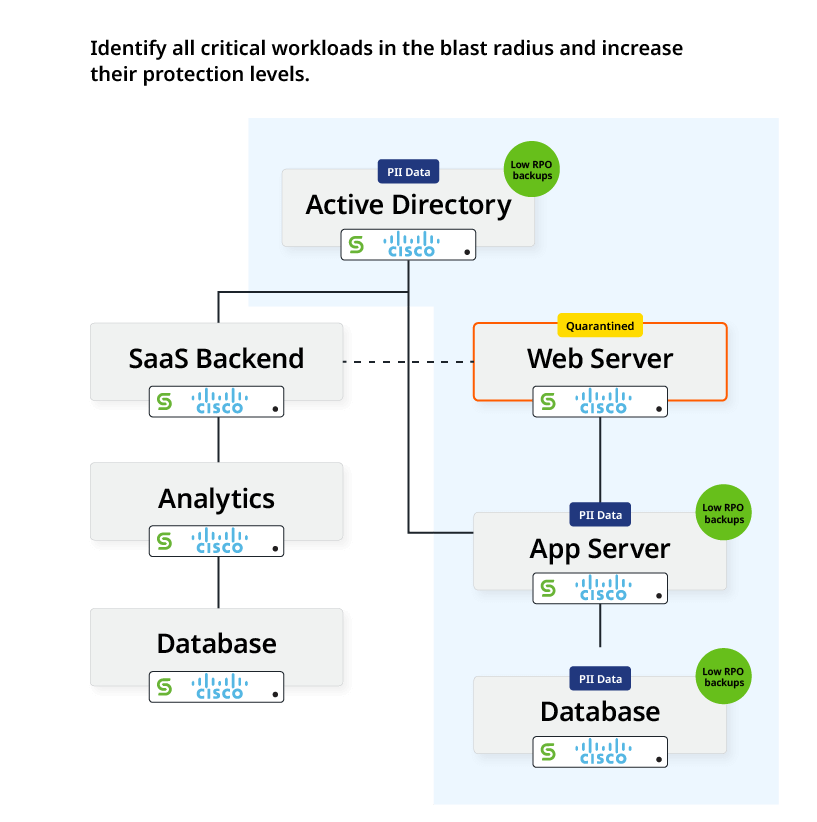
Second, Cisco XDR automatically moves to protect the most critical assets in the environment by taking an immediate snapshot of critical workloads and upgrades the protection policy for critical workloads to a more frequent cadence.
At the end of this stage, the RPO for critical workloads is set to the most aggressive level possible, to ensure data backups are as current as possible, thereby leading to a quick recovery with minimal data loss, if required.
Stage 3: Post-incident response
The next step depends on whether the attack was able to propagate through the environment. If the attack was detected and contained early enough, the malware can be successfully eradicated from the quarantined systems. However, in many cases, the attackers are successful in propagating their presence on multiple workloads, rendering the initial quarantine ineffective.
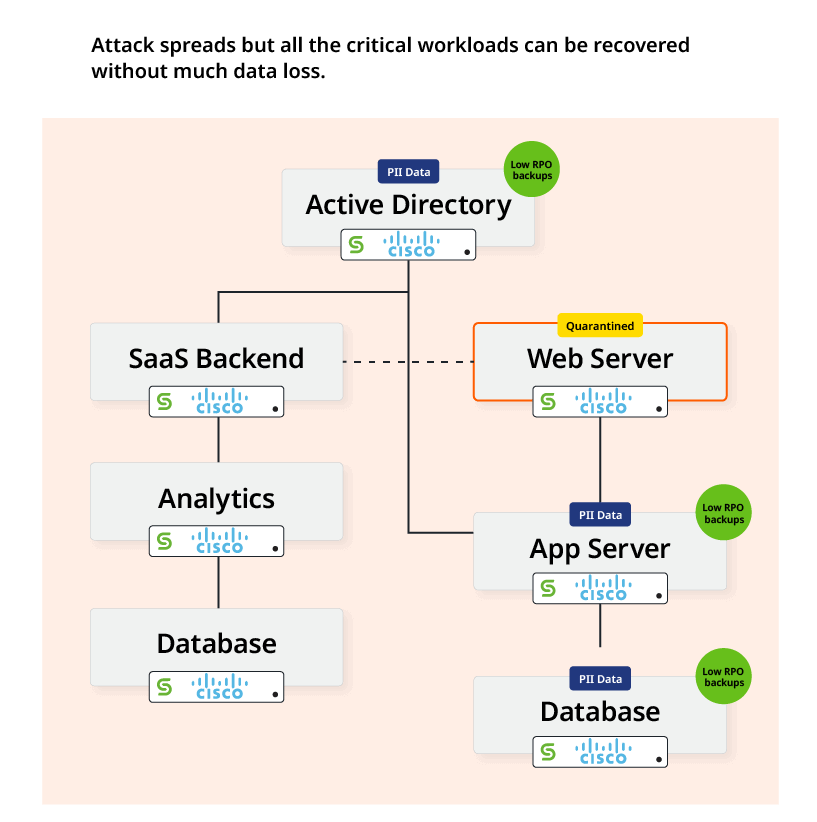
Scenario A: Attack not stopped in time. Ransomware detonates.
Let’s say the attacker was successful in laterally moving through the environment and detonating the ransomware, affecting large portions of the environment and bringing down several critical applications. The organization’s focus is now on accelerated and safe recovery. Incident response teams will focus on recovering critical workloads on priority. And thanks to the automatic backups taken during the early stages of the attack, data loss can be kept to a minimum if not zero.
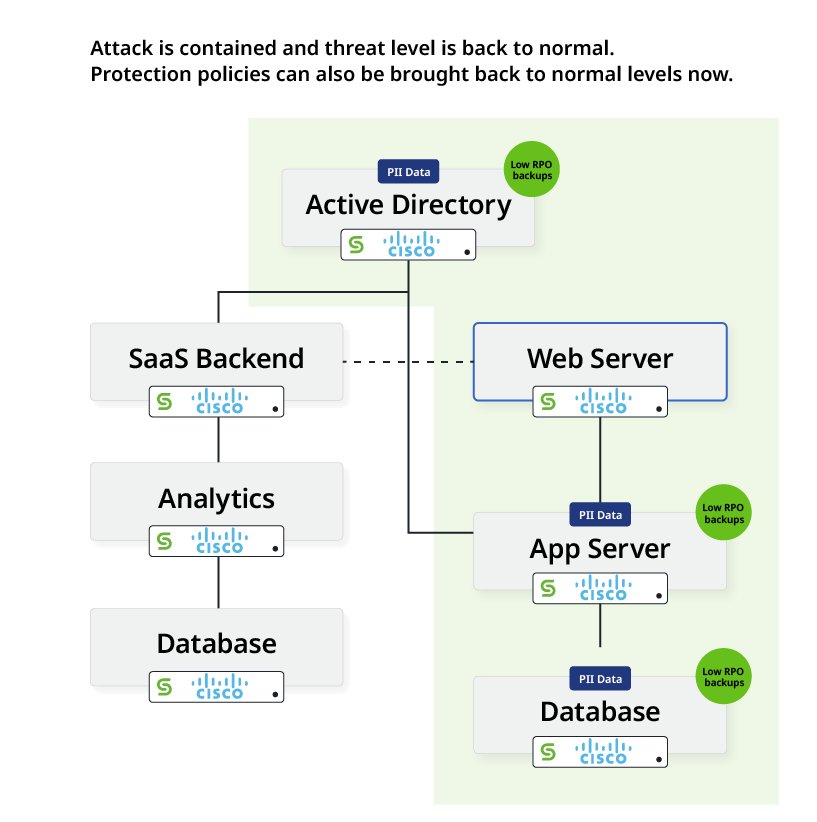
Scenario B: Attack successfully blocked
If the attack was successfully blocked, the solution (Cisco XDR and Cohesity integration) will revert the environment back to a steady state data protection policy.
Go faster to improve your security posture
Cyber resiliency is all about minimizing the disruption to an organization’s business processes and minimizing data loss during a cyberattack. Our integration with Cisco XDR helps InfoSec teams automatically capture a snapshot of business-critical information at the beginning of a ransomware outbreak, taking us one step closer to delivering a near-zero RPO during a catastrophic attack.