The global average cost of a data breach reached $4.88 million in 2024, according to IBM’s Cost of a Data Breach Report 2024.
The highest costs were in critical infrastructure organizations like financial services and healthcare. And for the 14th straight year, healthcare participants saw the highest breach costs—reaching $9.77 million. As hospitals and healthcare facilities embrace digital technologies to enhance care delivery and medical research, robust data security solutions are paramount. Protecting patient data is vital.
Like in medicine, prevention is key
With modern data security solutions, the goal is not merely to defend against cyber threats but to cultivate a culture of resilience where data protection is woven into the fabric of healthcare operations.
At its core, the journey towards digital security begins with a deep understanding of the risks we face. From ransomware attacks to data breaches, the threats are varied and ever-evolving. Yet, armed with knowledge and foresight, healthcare organizations can take proactive measures to mitigate these risks and safeguard patient data.
One such measure involves adopting modern data security solutions that offer comprehensive protection across the healthcare ecosystem. These solutions use advanced technologies such as machine learning and encryption to detect threats before they can inflict harm. By implementing robust access controls, encryption protocols, and real-time monitoring capabilities, healthcare organizations can create a formidable defense against cyber adversaries.
A modern data security blueprint architecture for healthcare
While modern data security is the key to resilience for healthcare enterprises, getting the right data availability architecture is key for a few reasons.
- It ensures timely access to accurate patient information, directly impacting the quality and safety of patient care. Rapid access to patient data is crucial for coordinating emergency response efforts and ensuring continuity of care during emergencies.
- For healthcare organizations, compliance with regulatory requirements, such as HIPAA and GDPR, necessitates robust data availability measures to protect patient privacy and security.
Given the criticality of data availability, it is imperative for healthcare enterprises to integrate backup, replication, archival, long-term retention, and security mechanisms into the data availability architecture to:
- Ensure continuous access to critical patient data.
- Mitigate risks of data loss or downtime.
- Comply with regulatory requirements while maintaining the highest patient care and confidentiality standards.
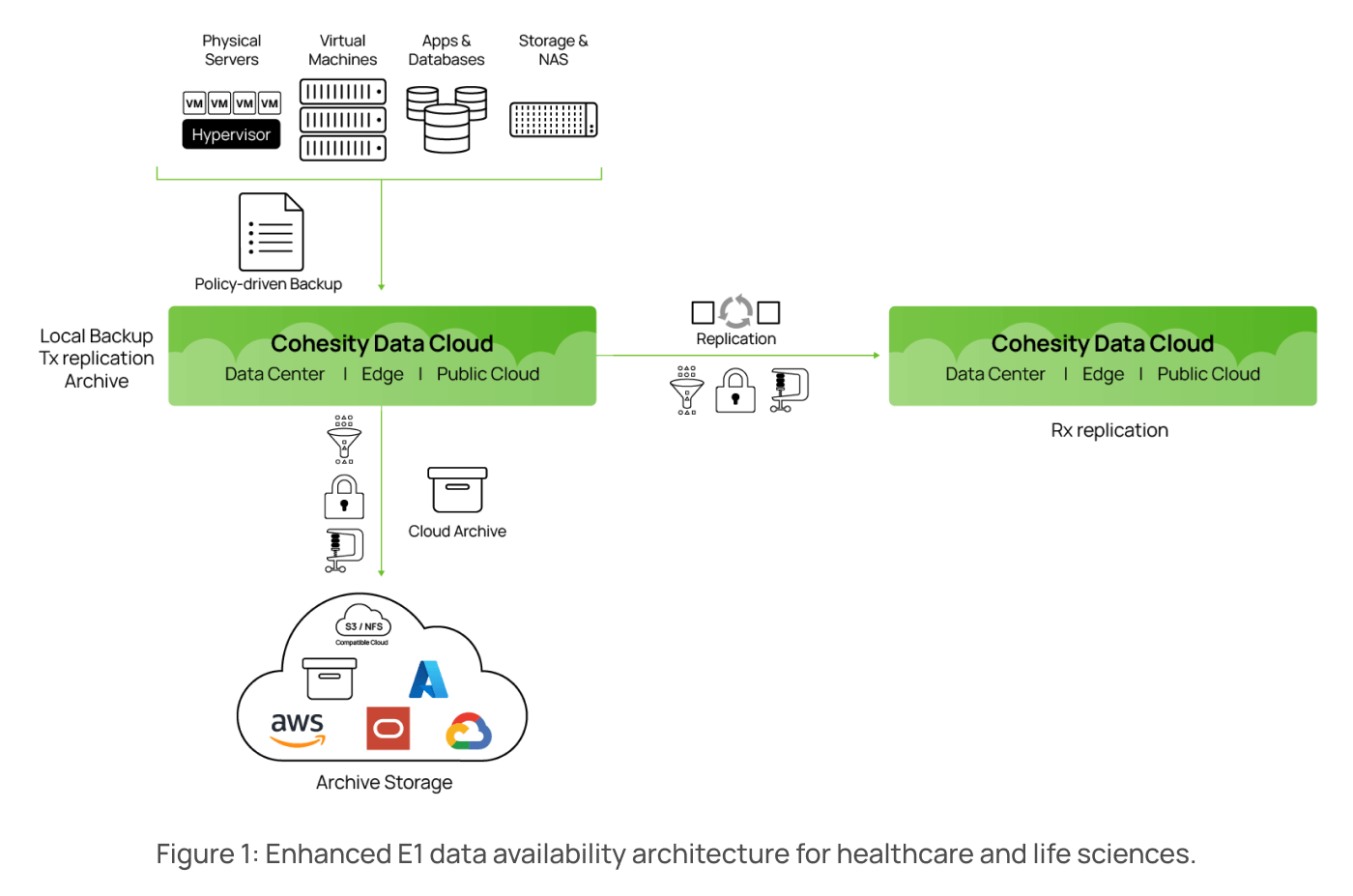
The hub and spoke architecture: Backup, replication, and archive
To transform the data estate, healthcare enterprises need a modern and proven architecture that outlines the critical design factors for maintaining the integrity, confidentiality, and availability of healthcare data.
The Enhanced – Backup, Replication, and Archive (Hub and Spoke) architecture is particularly well-suited for the healthcare industry due to its robust data protection features tailored to the sector’s unique needs. Healthcare organizations handle vast amounts of sensitive patient data that require stringent security measures and long-term retention to comply with HIPAA regulations. This topology ensures that data is backed up, replicated for redundancy, and archived for extended periods, providing a comprehensive safety net against data loss or corruption.
The hub and spoke model centralizes data management, making it easier for healthcare providers to streamline backup processes and ensure data consistency across multiple locations. By using this topology, healthcare organizations can enhance their disaster recovery capabilities, mitigate the risk of data breaches, and maintain continuous access to critical patient information.
This enhanced topology offers a holistic approach to data security and management, aligning perfectly with the healthcare industry’s requirements for confidentiality, integrity, and availability of patient data.
Get the blueprints to better business outcomes
We have assembled a guide consisting of recommended blueprints to make it easier and help you accelerate your ability to achieve better business outcomes while reducing risk and cost.
Learn more: