Frustration. Concern. Anxiety. Confusion. Disbelief. These are all natural emotions to feel during a cyberattack or any other major outage. What attackers focus most on, is fear. Not just any fear, but the kind of fear that comes from a complete loss of trust, further amplifies all of the other feelings to levels far beyond anything previously experienced. The question then becomes, how do you prepare to regain trust and have the confidence needed to respond and recover from a cyberattack?
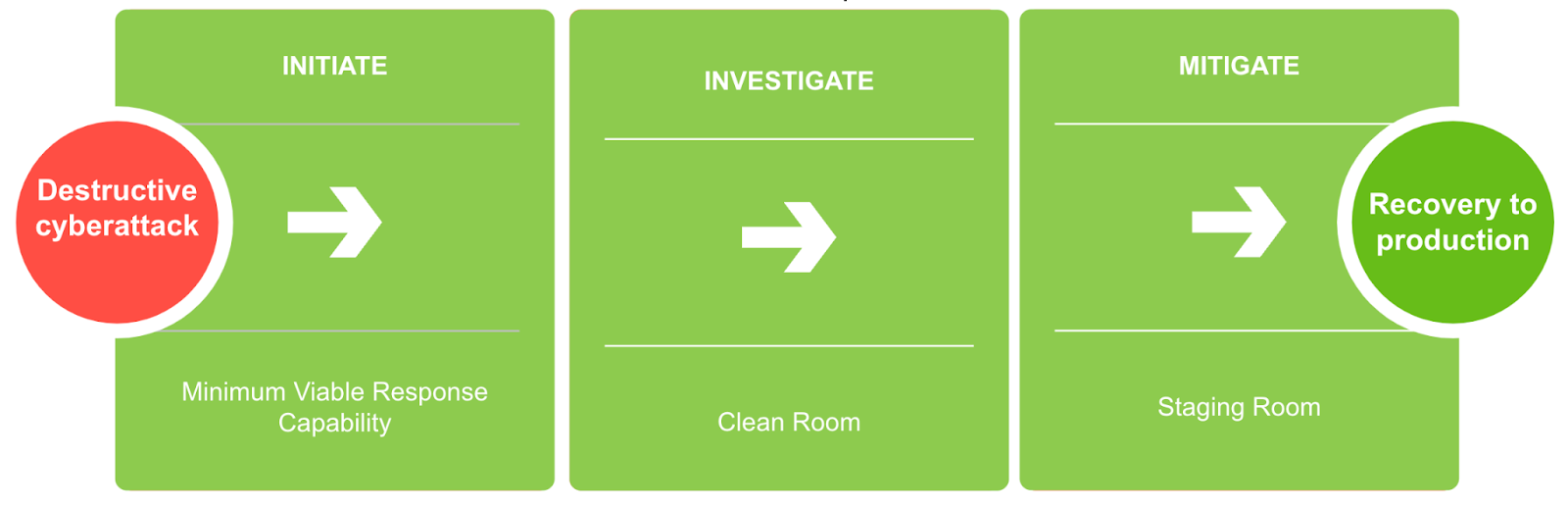
Answering this question was a prime driver for creating the Cohesity clean room design. Following industry best practices and in consultation with experts, we’ve assembled a set of product capabilities and workflows that organizations can use to achieve cyber resiliency in this age of destructive ransomware and wiper attacks. The design can be segmented into three stages that allow organizations to understand the scope of an attack and recover clean data into production.
What does the Cohesity clean room design deliver?
The design can be segmented into three stages (initiate, investigate, and mitigate) that allow organizations to understand the scope of an attack and recover clean data into production.
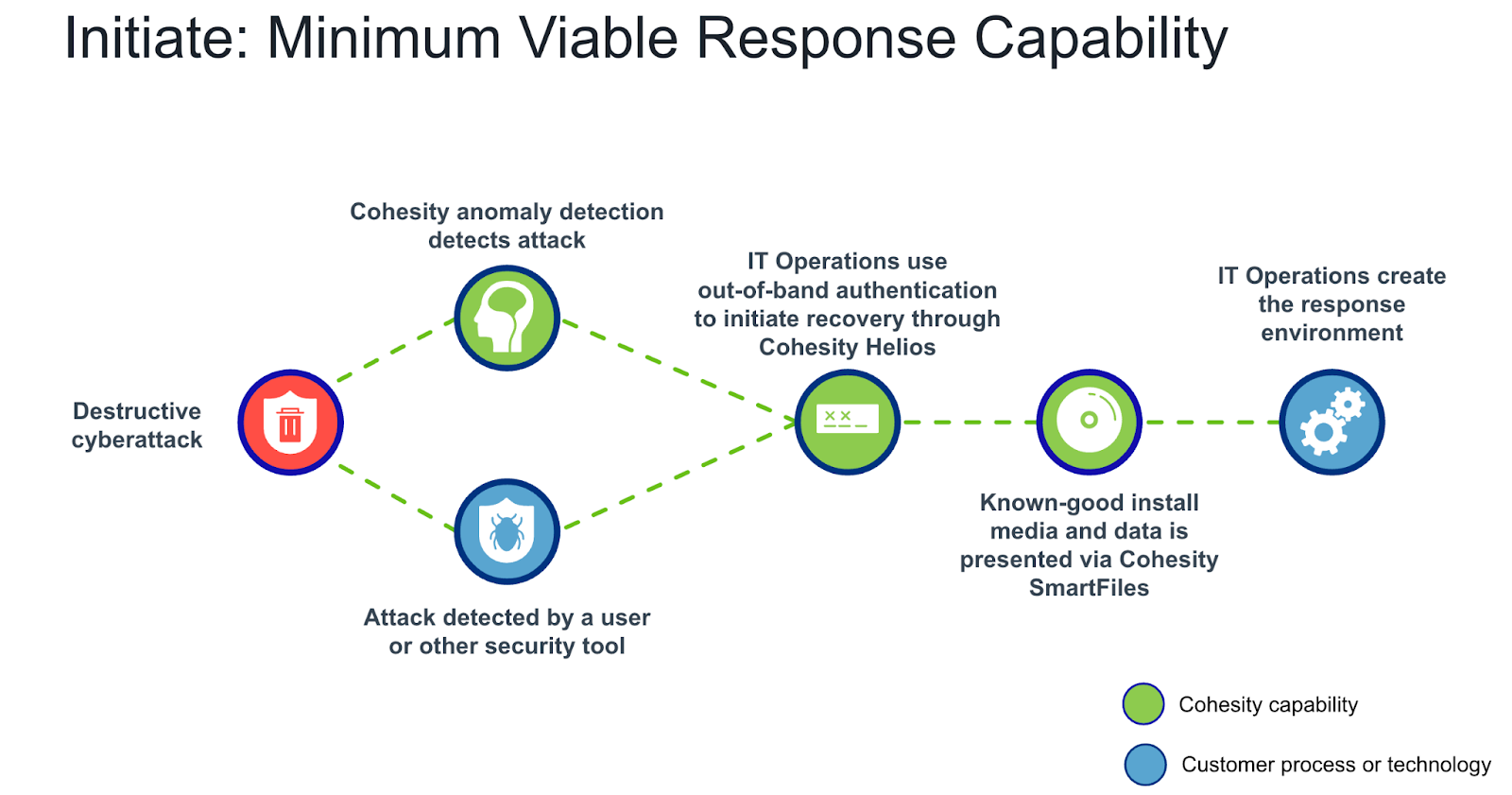
The first stage of restoring trust in your environment is to create a Minimum Viable Response Capability (MVRC) that allows you to bring critical systems online and begin the investigation. Without defining an MVRC, teams may not have access to communication such as email or even phones, which further hampers the response.
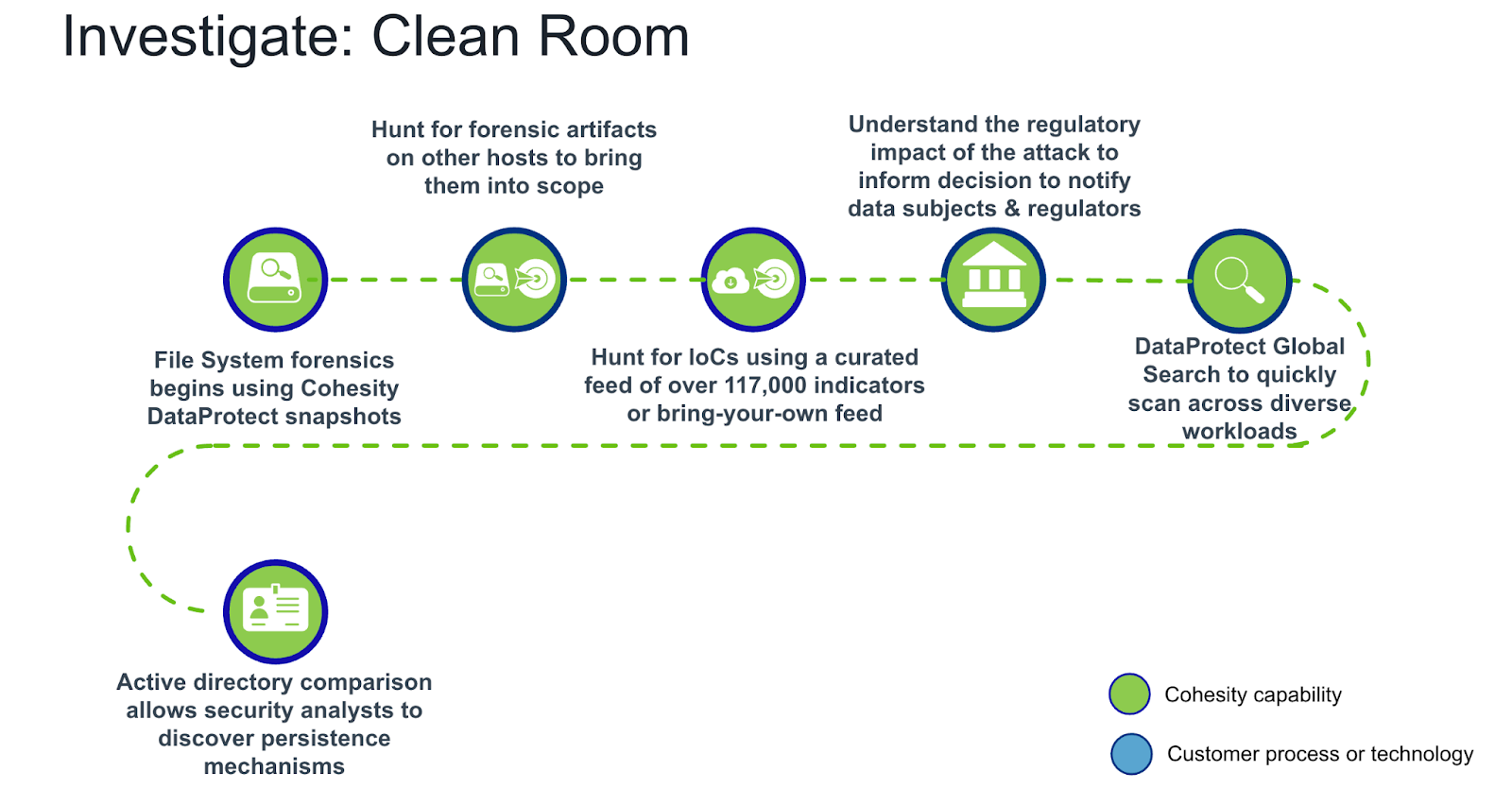
The second stage of the clean room design allows for the investigation into the attack to create a manifest of IoCs like files, registry keys, and user accounts that will be used during recovery to remove the threats and patch vulnerabilities that allowed the attack to be successful. Unfortunately, some have been led to believe that a cursory threat scan is all that’s needed to remove the threats, but this will inevitably cause malware to be reintroduced into the environment and extend the outage.
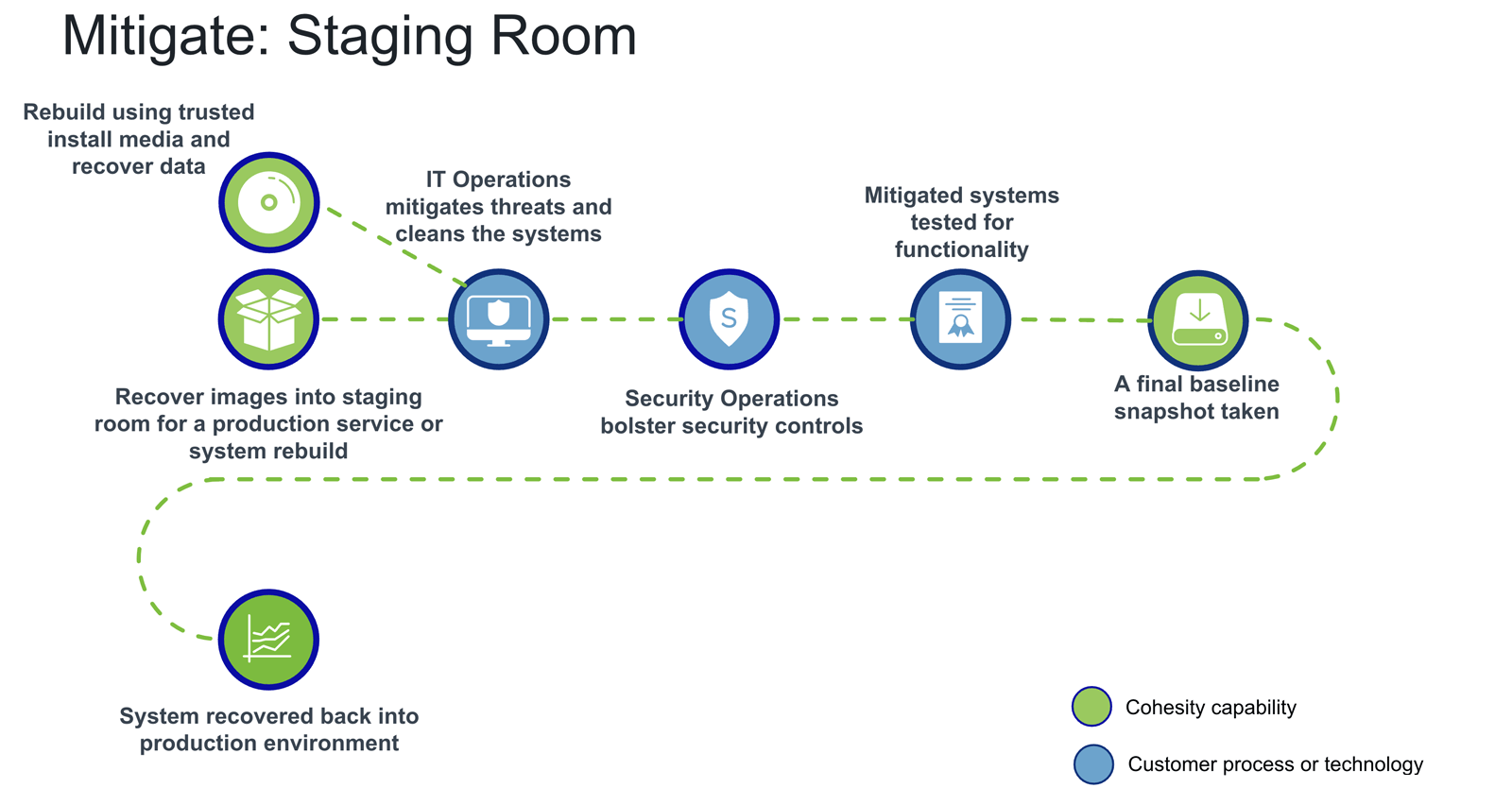
Once we understand the details of the attack, we can move to the next stage of mitigation, where threats can be removed and clean data recovered. During this stage, we understand what accounts we need to patch and remove. We will also define the security tools that will be improved to ensure similar attacks won’t get through.
Let’s dive a little deeper into each stage.
Minimum Viable Response Capability
The Cohesity clean room design allows organizations to build a “digital jump bag” of tools needed to create the MVRC using known-good software through Cohesity SmartFiles or Cohesity FortKnox. To define your digital jump bag, some planning will be needed, and you’ll need to ask some tough questions.
- If all access to the internal network is impacted, can you still initiate your IR plan?
- Is there a decision process and plan for remediation and rebuilding if authentication has been compromised?
- How will inventory details be made available in the above scenarios?
- What core systems and tools are needed to perform the initial triage, and is there a plan for where that will occur and how it will be initiated?
- How are tools impacted when authentication (AD, SSO, etc.), & DNS are unavailable?
- What are the scale limits of the current plan?
The last thing anyone wants to discover is they’re unable to get physical access to the building, the telephone systems are down because they use voice-over-IP, or the email systems are down without a plan to get them back.
Investigation in the clean room
Cohesity has several tools that will assist with investigating threats. Because the tools use backup data, they aren’t visible to attackers and are less likely to be disabled. Additionally, since the tools are out of band, it will be nearly impossible for attackers to know they’ve been discovered.
Among these tools are:
- The ability to hunt for IoCs using a curated feed of over 117,000 indicators
- Snapshots can be used to capture the state of impacted systems for investigation and evidence collection
- With Cohesity DataProtect, forensics investigators are now free to time-travel across the entire incident timeline, loading images of a file system state in seconds.
- During investigations, binaries can be extracted for detonation in sandboxes, producing more IoCs that can be fed into DataHawk’s threat-hunting capability
- By building relationships with leading security vendors through the Data Security Alliance (DSA), Cohesity is leading innovation in data-centric cyber response and recovery.
Mitigation, staging for recovery
Modern threats aren’t a “one size fits all” experience. During mitigation, a decision is made to either recover and “clean” the existing system or to rebuild and restore the data. By having an isolated staging area users are able to determine their path forward.
Either way, systems will be patched and tested to ensure no malware is being reintroduced and the system will function as expected. During this process, a final snapshot can be taken so if issues arise, the process won’t have to start from square one.
What’s next?
It doesn’t take much to destroy your trust in the systems you use every day. Part of our goal for securing the world’s data is to help you rebuild your trust in your systems so you can confidently respond to a cyberattack. Cohesity’s clean room design provides a trusted foundation that speeds up incident recovery and augments investigations by SecOps teams while minimizing the risk of secondary attacks. Our modular design creates an isolated environment in minutes, supporting the response and recovery process and allowing teams to mitigate threats faster.
To learn more, visit www.cohesity.com/solutions/clean-room/.