Restore trust in your network
Quickly create a Minimum Viable Recovery Environment (MVRE) to support the response and recovery process.
Don’t reinfect your network during restoration. Investigate and remediate attacks in an isolated environment using trusted tools—so you can find the root cause of an attack and recover clean data quickly.
Quickly create a Minimum Viable Recovery Environment (MVRE) to support the response and recovery process.
Provide the intelligence that incident responders need using native AI/ML threat-hunting tools and third-party tools in a safe, isolated environment.
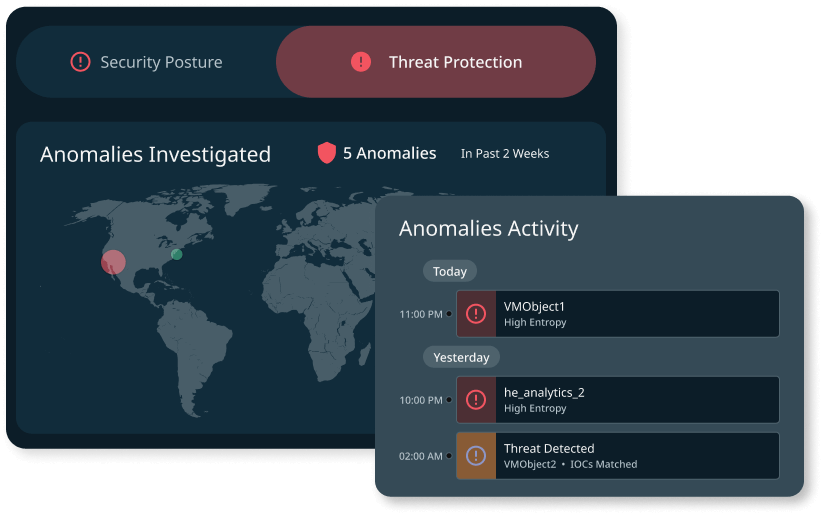
Expedite response with built-in threat analytics capabilities for insights into potential vulnerabilities and anomalies within the data.
Bring your Security Operations and IT Operations teams together in one trusted platform for all your data.
Flexible deployment options
Trusted storage for your incident response jump bag
Seamless interoperability through integrations with third-party tools and services
Be prepared for a cyberattack and simplify cyber investigations. Our clean room is designed to strengthen security and resilience against cyber threats so you can rebuild trust in your data.
Our clean room creates an isolated environment for detailed analysis of malware, so you can recover clean data faster. With a clean room, your organization can transition from a state where no data is available to one with fully operational production systems.
Thoroughly investigate the incident to understand its nature and impact. Reduce the risk of reinfection by determining what data has been compromised and what needs to be patched or rebuilt.
Eliminate the threat and implement enhanced controls based on the investigation’s findings. Help ensure systems are secure and data is clean while moving back into production.
Respond faster, recover smarter—because your business can't afford downtime

Knowledge is power—prepare for the inevitable. Uncover cyber risks and fortify your defenses now.

Our 3rd annual report examines the cyber resilience landscape across 8 countries.

Join Cohesity for a fully immersive 2-hour workshop created to simulate a live ransomware attack. Participants are invited to adopt the persona of a C-level decision-maker placed in the heart of ‘mission control’ of a fictional company.
