We’re excited to announce that the integration between Cohesity DataProtect and Cohesity DataHawk with Cisco XDR is now generally available. This solution empowers customers to respond at the onset of a ransomware attack by automatically capturing backup snapshots of critical data. This approach significantly reduces the recovery point objective (RPO) and minimizes business disruption. Using the backup snapshots, incident responders also gain a more granular context of file system changes, allowing forensic investigations to be more effective and efficient.
Overview of DataProtect, DataHawk, and Cisco XDR
Let’s take a look at the solution components:
Cohesity DataProtect is a modern backup and recovery solution that protects cloud-native, SaaS, and on-prem data at scale. Our unique backup and recovery capabilities improve RPO and minimize recovery time objective (RTO).
Cohesity DataHawk is a SaaS threat-protection solution. DataHawk works with Cohesity DataProtect to allow you to respond to cyberattacks and recover clean data.
Cisco XDR correlates data from disparate security tools, applying analytics and threat intelligence from Cisco Talos and others so analysts can prioritize and act against cyber threats. Cisco XDR leverages automation, guided response, and orchestration workflows to effectively prioritize and rapidly mitigate threats.
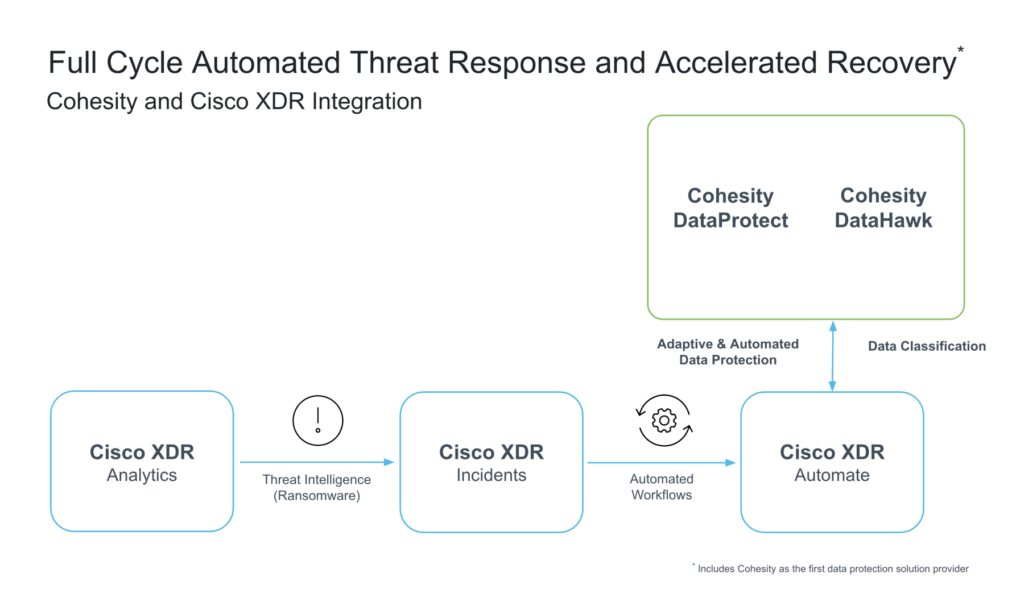
As we connected these solutions through APIs, we injected adaptive data protection into the Cisco XDR ransomware response playbook early and automatically.
Automated Cohesity workflows in Cisco XDR
The integration provides several workflows from Cohesity that you can install and use in Cisco XDR to trigger proactive protection and restore operations. Let’s examine two workflows triggered by an automation rule after an incident is created in Cisco XDR:
- Cohesity—Take Protection Group Snapshot for Affected VMs: Once triggered automatically, the workflow identifies all virtual machine assets mentioned in the incident. It uses DataProtect to take a backup snapshot using a Protection Group, which we’ll discuss in the next section, associated with the asset(s) mentioned in the incident.
- Cohesity—Identify Restore Point for Affected Virtual Machines: Once triggered automatically, the workflow retrieves the list of virtual machine assets associated with the incident and then determines the most recent and viable restore point for each virtual machine in DataProtect.
How the integration works during an attack
Let’s use the same real-world example described in our previous blog. Suppose you have a multi-tier web application that is connected to multiple critical workloads across multiple virtual machines (VMs) and have installed the two workflows discussed above in your Cisco XDR instance.
Referring to the above illustration, let’s say Cisco XDR Analytics detects suspicious activity on the Web Server and assigns it a high priority based on potential risk. Cisco XDR automatically creates an Incident in Cisco XDR, which then triggers automated workflows to run. In this instance, it makes an API call to identify viable restore points and enrich the incidents in the Worklog using the Cohesity – Identify Restore Point for Affected Virtual Machines workflow. Next, it triggers the Cohesity – Take Protection Group Snapshot for Affected VMs workflow to initiate a backup run of the whole Protection Group. This workflow takes a backup snapshot of both the potentially infected VM and the rest of the VMs in the Protection Group, enabling adaptive and automated data protection. Additionally, any data sensitivity information, identified by DataHawk’s data classification capabilities, associated with the virtual machine is added to the incident notes.
Protecting and securing your enterprise data with Cohesity
Now let’s look into how the capturing of a backup snapshot, or data protection, works.
A Protection Group is a backup job that runs repeatedly to back up data from a source and store it on a Cohesity cluster. A Protection Group uses the schedules and settings defined in a policy that defines when and how backups are captured, archived, or replicated. Typically, customers group together VMs that provide a similar function or support an application in one Protection Group, which could have anywhere from a single to hundreds of VMs in it.
When DataProtect is first deployed in a customer environment, a full backup of data sources is completed. This process includes creating one or more Protection Groups to back up the source.
In protecting data, Cohesity delivers the highest level of security against ransomware attacks because immutability is baked into Cohesity’s file system—SpanFS. Other security features include least privilege access delivered by granular role-based access control (RBAC), separation of duties delivered by Cohesity’s Quorum capabilities, and multifactor authentication (MFA) via different methods including Single Single-On (SSO). Cohesity simplifies secure access to our clusters via SSO authentication by integrating with Cisco Duo as well as other major identity provider (IdP) vendors.
When an Incident triggers an API call to Cohesity to run the Cohesity – Take Protection Group Snapshot for Affected VMs workflow, Cohesity executes an incremental backup of the Protection Group, capturing only new data since the last incremental was run.
In the next section, let’s explore how you can use these backup snapshots to help accelerate response and recovery activities for your organization.
Accelerating forensics and clean data recovery and minimizing the RPO
Remember that a backup snapshot of both the potentially infected VM and the whole Protection Group that it belongs to is taken when the Cohesity – Take Protection Group Snapshot for Affected VMs workflow is triggered.
The backup snapshot(s) of the potentially infected VM gives you an artifact to support forensic analysis. Using Cohesity’s copy data management technology, you can instantiate clones from the backup to a clean room or a secure and isolated environment to allow digital forensics and incident response teams to investigate file system changes at a very granular level across the entire potential incident timeline. These valuable backups therefore allow you to travel on the incident timeline and increase the efficiency of your response capabilities, which in turn helps reduce your recovery time objective (RTO).
In a normal recovery, the backup snapshot of the other workloads in that same Protection Group allows you to accelerate response and recovery activities, thus minimizing the RPO and reducing RTOs. In the case of a cyberattack where ransomware has brought down multiple critical applications, your IT and security teams are now armed with a very recent backup for these workloads that they can restore from after verifying the data is clean. The result: you dramatically reduce your data loss and accelerate your recovery journey.
Get the integration through the Cohesity Marketplace. Combine the power of this solution with the fast backup and recovery throughput of Cisco UCS® X-Series Modular Systems, certified with Cohesity DataProtect, to get the fastest possible recovery time. Explore all other integrated Cohesity and Cisco solutions at www.cohesity.com/solutions/technology-partners/cisco/ and stay tuned for the next implementation of this integration.