What is a ransomware attack?
A ransomware attack consists of malicious software code and actions used by an individual, group, or nation-state to render another person’s or organization’s electronic data or systems unusable via encryption—unless the victim pays the attacker’s demanded sum of money (“the ransom”) to get it back.
Ransomware is malware created specifically by threat actors to take advantage of technology and human vulnerabilities to achieve financial gain. Ransomware attacks have evolved—from attacks on production and backup systems to data exfiltration—while becoming more prevalent because more companies are paying for decryption keys to unlock their data. The most successful ransomware attacks have resulted in millions of dollars in losses to organizations worldwide.
How do ransomware attacks happen?
Ransomware attacks happen because people and systems are vulnerable. Cybercriminals are inventive and patient, continually targeting digital assets with ransomware until they find a way in—often by someone clicking on an infected link or attachment (a phishing attack), compromised credentials, or a system vulnerability. Every person and organization relying on digital technology is a potential ransomware target which is how ransomware attacks happen.
How to prevent and protect against ransomware attacks?
The best ways to prevent and protect against ransomware attacks are to put people, processes and technologies in place to defend sensitive data. These include:
- Educating and training employees to raise ransomware awareness and prevention
- Establishing a ransomware prevention plan and practicing its steps
- Utilize AI/ML-enabled cybersecurity solutions
- Modernizing data security and data management solutions with ML/AI-driven backup and recovery
How to recover from a ransomware attack
A successful ransomware attack doesn’t have to be devastating to a business.
If cybersecurity is breached, organizations that take advantage of modern data security and data management can ensure rapid recovery of data at scale—while refusing to pay ransom. They can have peace of mind with instant recovery capabilities that allow them to rapidly restore hundreds of VMs, large databases or large volumes of unstructured data instantly, at scale, to any point in time and location. They can be confident data they are using to recover quickly is also free from potential ransomware because a built-in machine learning (ML) engine can recommend the last known clean copy for restore. This not only prevents malware reinjection but accelerates recovery time and if it allows you to recover data directly in-place on the same platform—without spinning up a new server or database. That’s a time-saver for forensics, too.
How to defend against ransomware attacks
Organizations with robust, modern backup and recovery best defend against ransomware attacks because they have global visibility into data and advanced security built on Zero Trust principles. Capabilities such as immutable snapshots, data encryption, write once, read many (WORM), configuration auditing and scanning, and fault tolerance, threat protection, as well as flexible data isolation add defense in depth to their environments.
Organizations with modern data management lower data theft and loss risks by more effectively stopping unauthorized access through multi factor authentication, monitored modification, granular and role-based access control.
How to detect ransomware attacks
Organizations can best detect ransomware attacks by using a data security and data management solution powered by artificial intelligence and machine learning (AI/ML).
These capabilities deliver advanced anomaly detection with threat intelligence and scanning to quickly determine unusual patterns that can signal a ransomware attack and automatically alert teams about them. A platform with extensible APIs is another secret weapon in the defense of data against ransomware because teams can easily integrate other detection capabilities such as virus scanning, data masking, file audit logs analysis and data classification to counter ransomware attacks.
Why are ransomware attacks becoming more common?
The rising popularity of ransomware attacks is linked to three economic trends:
- Hybrid work policies — When organizations were forced to pivot to supporting employees at home, ransomware attackers went to work. They found new vulnerabilities in endpoints that were no longer secured as well as they had been in office environments.
- Cryptocurrency adoption — Bad actors typically launch ransomware attacks anonymously then demand untraceable payments to easily collect ransom. Even with new scrutiny on cryptocurrency, ransomware attacks continue to increase in frequency and velocity.
- Increasing ransom payments — Bad actors have experienced financial windfalls from organizations willingness to pay to get their data back. That behavior encourages other cybercriminals to get into the ransomware business.
Ransomware attack history: Examples of the biggest ransomware attacks
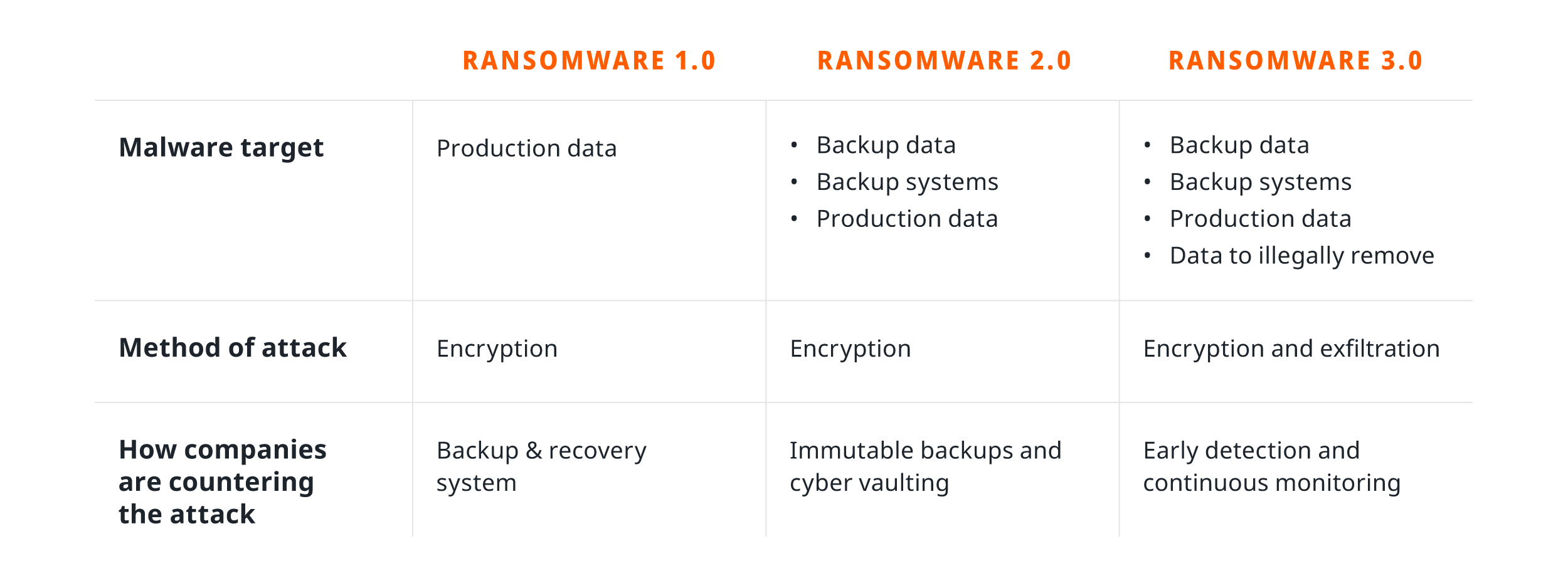
Ransomware attacks have evolved. To date, organizations fighting back against ransomware have been battling three distinct variants:
Ransomware 1.0 — Bad actors using malware to target and encrypt production data. Crypto ransomware was a popular 1.0 variant in the WannaCry and TeslaCrypt attacks, with estimated losses in single digit billions of dollars.
Ransomware 2.0 — Using ransomware, cybercriminals aggressively attack the backup data stored on existing backup infrastructure hardware. This malware disables or deletes backup solution data, security services, and critical Microsoft services like VSS, SQL Server prior to starting an attack on production copies of data. Locker (from DarkSide) and Ryuk (from Wizard Spider) are popular 2.0 variants. The former garnered headlines in 2021 when it took down the Colonial Pipeline Company servicing the southeastern United States with the company paying more than $4 million.
Ransomware 3.0 — Bad actors not only perform the standard data encryption of a sizable data set, they also exfiltrate proprietary and customer data in a double-extortion ransomware scheme. REvil is a popular ransomware 3.0 variant and it is the malware behind the largest known cyber ransom demanded to date: $50M from a global computer manufacturer in Asia.
Cohesity and ransomware attack
Cohesity excels at countering ransomware attacks. With platform, application, and third-party integration capabilities, Cohesity data security and data management stops cybercriminals and boosts cyber resilience with end-to-end:
Protection — Cohesity protects data using Zero-Trust principles, enforces strict access and administrative controls, and comes standard with FIPS encryption and MFA, plus native immutability.
Detection — Cohesity lowers risk by giving organizations anomaly detection, user behavior monitoring, and threat detection. Teams can respond and remediate fast using anomaly detection and integrated security operations and incident response. With threat protection, organizations can also scan backup data for indicators of compromise (IOCs) that can indicate ransomware activity.
Recovery at scale — Cohesity gets teams back to business fast by ensuring clean data—scanned correctly and quickly—is repurposed and a wide variety of data sources (virtual machines, databases, and NAS data) is instantly recovered to any backup point in time and location without downtime and data loss.
Access the Ransomware Readiness Guide for more information.