Not a play on my surname, “Shields Up” refers to a new warning from the Cybersecurity and Infrastructure Security Agency (CISA) of the United States government, strongly urging companies to be prepared for current and future potential threats. The current world environment creates a significant increase in cybersecurity risk.
The guidance includes several recommendations for backup and recovery, notably “ensure that backups are isolated from network connections.”
The threat of ransomware and other cyberattacks places a unique focus on how organizations leverage their backup data. If a ransomware or other attack corrupts production data, organizations need to recover rapidly and accurately to support their 24×7 operational needs. Moreover, as ransomware targets backup data itself, additional backup safeguards and isolation techniques must be employed.
The need for additional security has led to discussions about using air gap approaches to help counter the threat of ransomware. While a traditional air gap approach (e.g., tape out) provides excellent security for data it does not support rapid recovery.
Other isolation techniques include cloud archive, backup as a service, and disaster recovery as a service. Each of these have their unique use cases but do not provide the balance of security AND agility that organizations need to rapidly recover clean data when a ransomware attack occurs.
To support demanding RPO/RTO requirements, new data isolation techniques have emerged as an effective alternative to support cyber resiliency; with an isolated copy of the backup data stored in the cloud or another location with temporary, but highly secure connections. This provides a tamper-resistant environment to defend against ransomware and other cyberattacks, insider threats, and natural disasters.
Limits of the Traditional Air Gap
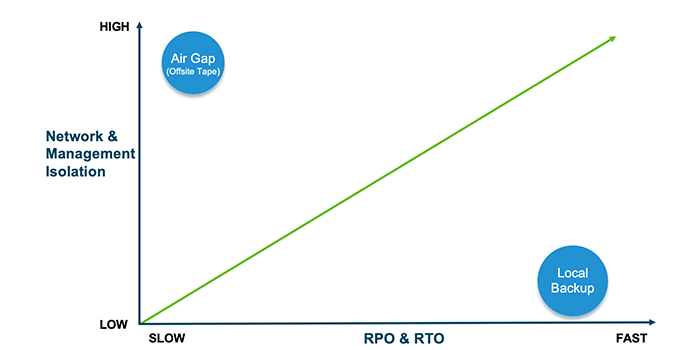
While the air gap is the best case of data isolation, it comes with a cost—lack of agility. An air gap provides excellent security, but the physical and electronic isolation limits the frequency of backups and the ability to quickly restore operations.
What organizations need is a balance between isolation and RPO/RTO. As shown in the graph below, isolation provides the best security and local backups provide the best RPO/RTO—the combination of their characteristics represented by the green line is what organizations need—balanced security and speed.
Agile Approaches for Data Isolation
Sometimes referred to as virtual air gaps, new data isolation techniques can provide the balance of isolation and RTO/RPO required by today’s operating environments. New data isolation techniques integrate tamper-resistant, highly available recovery data that is physically isolated with a highly secure and temporary network connection. The network connection leverages a multi-layered, zero-trust methodology to limit access to the isolated data.
Tamper resistance is provided by the following safeguards:
- Immutable snapshots – A gold copy of isolated data never exposed nor mounted externally
- DataLock – A time-bound, WORM lock on the backup snapshot that can’t be modified
- Quorum – Multiple personnel must approve requests for recovery of data to prevent illegal access
The connection is safeguarded by the following controls:
- Virtual air gap – Configurable transfer window, outside of which vault is locked
- Encryption – Data is encrypted at rest and in-flight
- Role-based access control (RBAC) – Granular admin and user access can be implemented on
least privilege and need-to-know principles
- No back door – Support account enablement by authorized customer users only
- Secure SSH access – A secure access path over an unsecured network
With these capabilities, organizations can select the data isolation technique that meets their operating goals. These techniques include the following (and are supported by the Cohesity Helios Platform):
- Protected replication to a remote cluster – Customers can replicate from one immutable Cohesity cluster to another remote cluster, running either on-premises or as virtual clusters. Compared to the legacy data isolation approach that requires shipping tapes off-site, this data isolation method lowers RTOs and RPOs as data on the remote cluster is readily available.
- Protected replication to a NAS target – Cohesity archives data to a NAS external storage target that supports WORM for isolating data with lower RTOs and RPOs.
- Protected replication to cloud – To take advantage of the public cloud’s scale and elasticity, organizations have been leveraging cloud as one of the modern ways to achieve data isolation. Cohesity supports archiving to the cloud to achieve data isolation and immutability, lower RTOs and RPOs, and lower TCO.
Cohesity FortKnox is our upcoming SaaS solution that will allow customers to maintain an isolated copy of their data in a Cohesity-managed cloud vault to improve data resiliency in the face of ransomware attacks. This immutable copy of data can be quickly and easily recovered back to source or an alternate location, in case of a ransomware attack. In addition to immutability, this gives customers another means to thwart attackers trying to encrypt data.
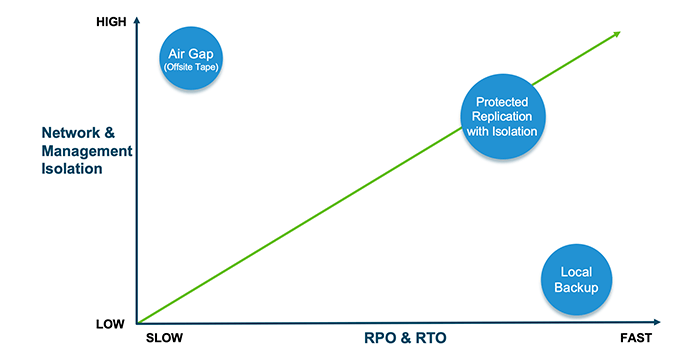
The foregoing isolation techniques provide the perfect balance of isolation and RPO/RTO for organizations to meet their operating objectives; allowing them to to quickly recover from cyber security incidents while supporting SLAs and improving cyber resilience. This relationship is exhibited in the graph below, showing protected replication with isolation as the preferred approach:
Updating the 3-2-1 Rule for the Modern Enterprise
The 3-2-1 rule says there should be at least three copies of your data, on two different media and one of them off-site at all times. To keep up with modern enterprise imperatives, the off-site copy could be an isolated replication to provide a protected AND agile copy of data to enable rapid recovery from ransomware or other attacks.
Balance is the Key
The balance of RTO/RPO and isolation provide the optimal result for organizations seeking to have cyber resiliency that meets their organizational objectives. New data isolation techniques provide additional protection to the organization in addition to existing backup and recovery or disaster recovery (DR) processes. The outcomes are stronger data protection and security strategies, reducing the risk of disruption to business continuity.
Not an Option: Shields Up
The CISA warning provides unambiguous guidance on data isolation; while not a legal requirement, no one should consider this optional. Organizations should take heed or risk disruption to their operations. Given the CISA guidance and evolving best practices for ransomware defense, data isolation is certainly a fundamental and reasonable counter measure, as essential as passwords.